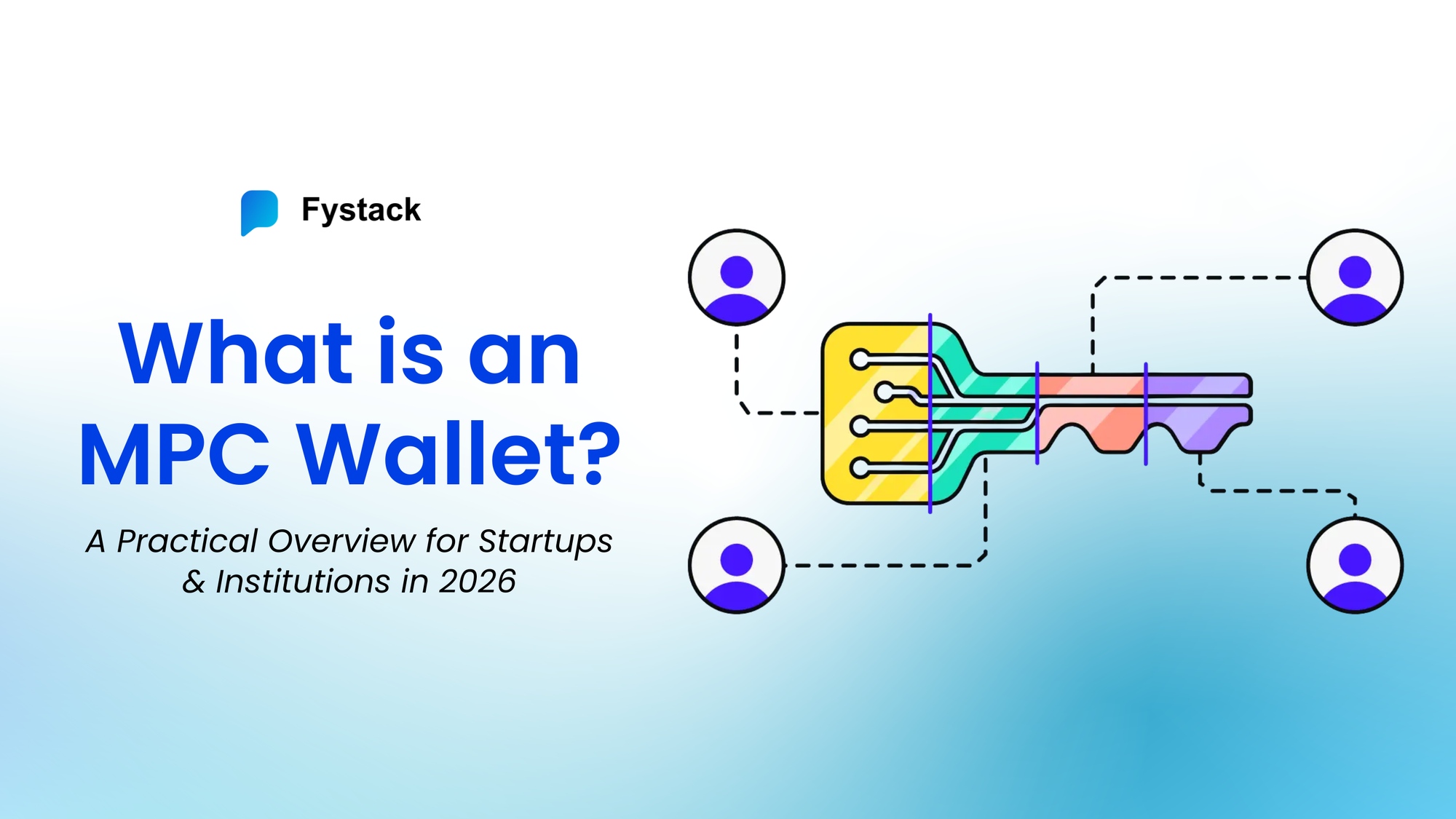
What is an MPC Wallet? A Practical Overview for Startups & Institutions in 2026
Phoebe Duong
Author
In the early days of Web3, the private key was considered absolute ownership. By 2026, for enterprises and serious startups, it has become the most dangerous single point of failure.
A lost seed phrase, a compromised device, or mismanaged access rights can permanently freeze funds or disrupt mission-critical business operations. This risk model no longer aligns with how modern organizations manage payments, treasury, and digital assets at scale.
As blockchain adoption expands into enterprise payments, fintech infrastructure, and institutional custody, wallet security is no longer a user problem. It has become a systems and governance problem.
By 2026, the shift is clear. Enterprises are no longer asking, “What is an MPC wallet?” They are asking, “How do we implement an MPC wallet correctly?”
Today’s conversations focus on architecture and control, not definitions:
- Self-hosted MPC wallets vs SaaS custody models
- Reducing operational and insider risk
- Supporting multi-chain treasury and stablecoin payment rails
- Avoiding long-term custody and vendor lock-in
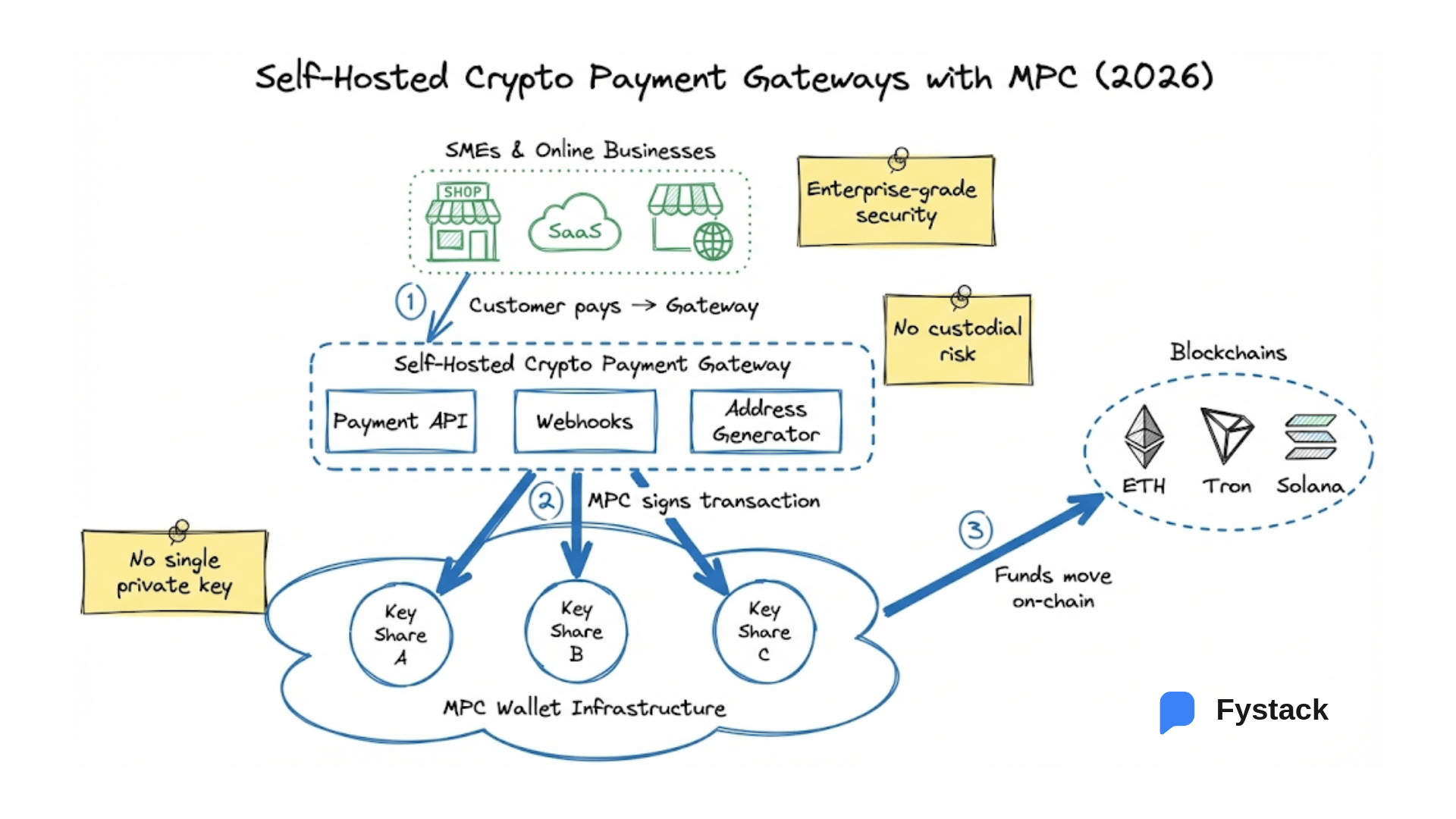
This shift is especially visible in enterprise stablecoin payment flows, where MPC wallets are increasingly used to support B2B reconciliation, treasury automation, and cross-border settlement at scale.
This marks a new phase for wallet infrastructure.
MPC wallets are no longer just a security feature - they are becoming the default foundation for enterprise-grade Web3 systems.
Many organizations now treat MPC wallets as a baseline requirement for modern deployments. This shift toward infrastructure ownership is explored further in Fystack’s analysis of why self-hosted MPC is becoming the new standard for 2026, especially for enterprises that require full control over keys, data, and recovery.
What this guide covers
This article is designed as a pillar page for MPC wallets in 2026. It provides a high-level, practical overview of MPC wallet infrastructure, while linking to deeper technical and architectural resources where needed.
Rather than focusing on cryptographic theory, this guide approaches the MPC wallet from a business, systems, and operational perspective - how enterprises and serious startups actually evaluate and deploy it in production.
Readers will gain:
- A clear understanding of MPC wallet architecture from an enterprise and governance standpoint
- A practical comparison between MPC wallets, multisig wallets, and cold storage models
- A framework for evaluating SaaS MPC custody vs self-hosted MPC infrastructure
- Insight into how MPC wallets integrate with account abstraction and next-generation smart accounts
Each section focuses on strategic understanding, not low-level cryptography.
Where deeper detail is required, the guide points to dedicated Fystack articles covering MPC infrastructure, custody models, and implementation best practices.
What Is an MPC Wallet?
An MPC wallet (Multi-Party Computation wallet) is a wallet architecture that replaces a single private key with multiple independent key shares, distributed across different systems, devices, or organizational domains.
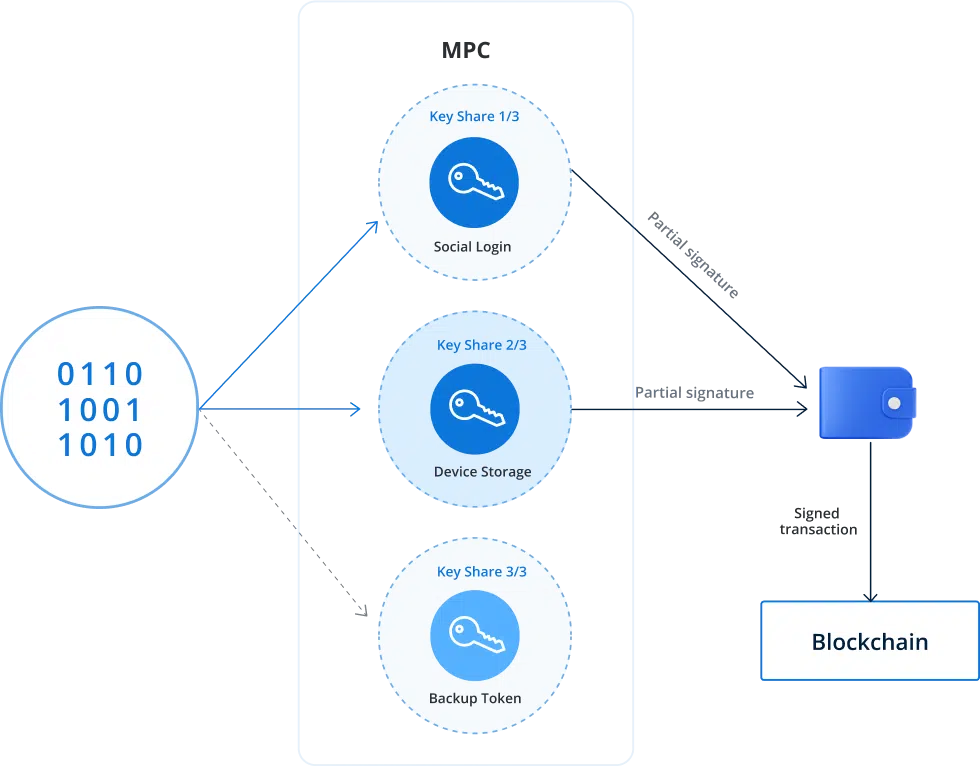
Instead of relying on one secret to control assets, an MPC wallet requires a predefined threshold of key shares to jointly authorize a transaction without ever reconstructing the full private key at any point.
This design removes the single point of failure inherent in traditional wallets and makes MPC wallets suitable for enterprise-grade security, governance, and scale.
Traditional wallets assume that one private key or seed phrase can be securely stored and managed indefinitely. That assumption breaks down quickly in real-world enterprise environments where multiple teams, systems, and operational workflows are involved.
An MPC wallet replaces that assumption with key sharding by design.
Control is split across isolated environments, such as:
- An application or user-facing layer
- A backend signing or policy engine
- A separate recovery or governance system
No single key share can move funds on its own. Authorization only occurs when the required parties collaborate according to predefined policies.
This is why MPC wallets are often described as “seedless by design.”
There is no master private key to leak, lose, or mishandle.
For enterprises and startups managing payments, treasury operations, or embedded wallets, MPC wallets fundamentally change the risk model:
- Single-key failure is eliminated
- Duties can be separated across teams and systems
- Governance logic is enforced cryptographically, not manually
- Operations remain resilient even if one component is compromised
Rather than treating wallet security as an end-user responsibility, an MPC wallet allows organizations to treat custody as infrastructure - aligned with how modern enterprises already manage access control, approvals, and operational risk.
For readers who want a deeper architectural explanation of how MPC wallets evolved from cryptographic theory into production infrastructure, Fystack covers this transition in comprehensive guide to MPC wallet infrastructure.
What is an MPC wallet, and how does it differ from traditional crypto wallets?
An MPC wallet uses distributed key generation and signing, where no single entity ever holds the full private key. This fundamentally differs from traditional wallets that rely on single key custody.
Why are MPC wallets considered enterprise grade infrastructure?
MPC wallets support governance controls such as role based access, approval workflows, policy enforcement, and auditability. These capabilities are required for managing corporate funds.
How does MPC improve security without relying on cold storage?
MPC removes private key exposure entirely. It enables secure transaction signing without offline storage, manual key handling, or operational bottlenecks.
Are MPC wallets custodial or non custodial?
MPC wallets can be custodial, non custodial, or hybrid, depending on how signing parties and control policies are structured at the infrastructure level.
What enterprise risks do MPC wallets primarily mitigate?
MPC wallets reduce risks related to key compromise, insider threats, operational errors, and single user dependency. These are common failure points in legacy wallet models.
How MPC Wallets Work Behind the Scenes
At a high level, an MPC wallet works by distributing cryptographic control across multiple independent parties, instead of relying on a single private key.
Rather than protecting one secret at all costs, MPC wallets operate on distributed key shares that collaborate to authorize transactions, while the full private key is never reconstructed or exposed at any point.
This architecture enables enterprises to enforce control, approvals, and governance without placing trust in any single system, device, or individual.
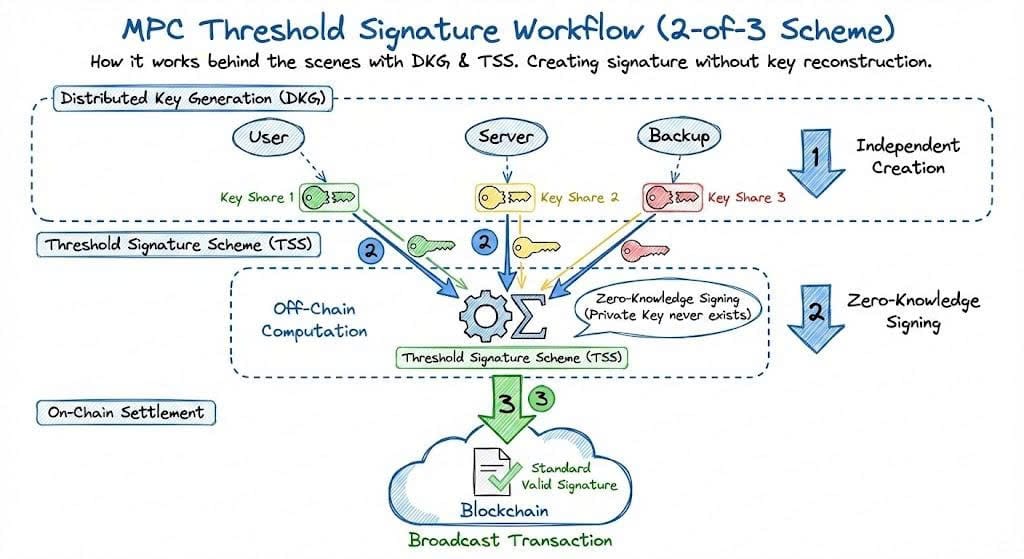
The Core Building Blocks
MPC wallets rely on two foundational mechanisms:
- Distributed Key Generation (DKG)
Key shares are generated collaboratively from the beginning. No party ever creates or holds a full private key. - Threshold Signature Schemes (TSS)
Only a predefined subset of key shares is required to authorize a transaction, based on enterprise policy.
Together, these mechanisms ensure that no single component can move funds alone, even if it is compromised.
A Simple Mental Model for Decision Makers
An MPC wallet functions similarly to enterprise approval systems already used in traditional finance.
Control is distributed.
Authority is shared.
Execution only happens when policy conditions are met.
From an operational perspective:
- Devices, backend services, and governance systems act as independent participants
- Key shares represent authorization power
- Transactions are executed only when required parties collaborate
This model aligns naturally with separation of duties, internal controls, and audit requirements expected in enterprise environments.
Why MPC Wallets Operate Off-Chain
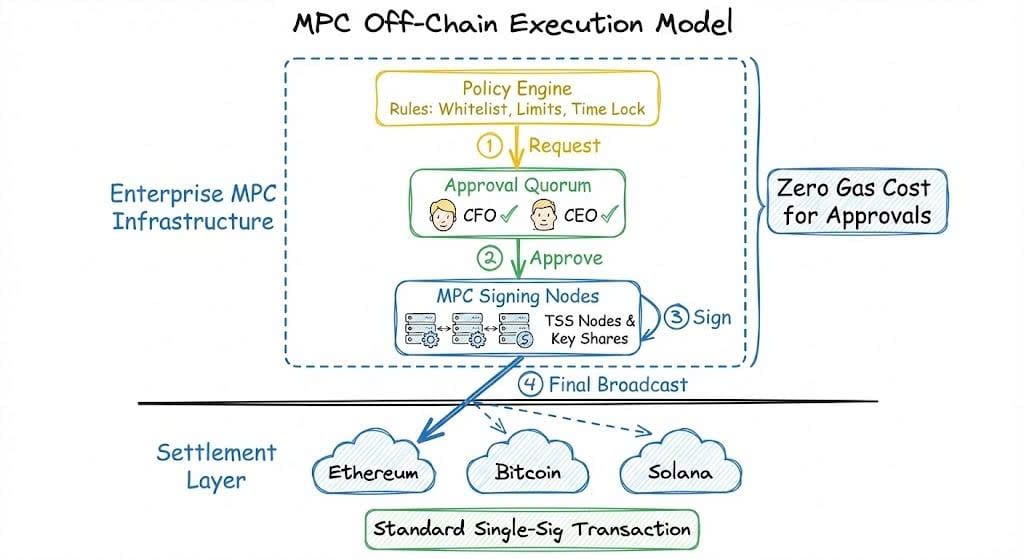
One of the most important characteristics of an MPC wallet is that all signing logic happens off-chain, at the cryptographic layer.
This has several direct implications for enterprise systems:
- The blockchain only sees a standard single-signature transaction
- Gas costs remain low and predictable
- Internal approval logic and governance policies remain private
- The same MPC wallet architecture works across multiple chains
As a result, MPC wallets are chain-agnostic infrastructure, not chain-specific tooling.
MPC Wallet Execution Model
| Dimension | MPC Wallet |
|---|---|
| Signing location | Off-chain (cryptographic layer) |
| On-chain footprint | Standard single-signature transaction |
| Governance visibility | Private, off-chain |
| Chain compatibility | Multi-chain (EVM & non-EVM) |
| Transaction latency | Near real-time |
This execution model is why MPC wallets are widely adopted for enterprise payments, treasury operations, and automated settlement flows.
For teams that want to go deeper into system design, Fystack provides a technical walkthrough of open-source MPC wallet infrastructure and modular MPC architecture.
Why are personal wallets unsuitable for managing corporate funds?
Personal wallets lack governance, segregation of duties, approval controls, and audit trails. This makes them incompatible with enterprise treasury operations.
How do MPC wallets act as a governance layer for enterprises?
MPC wallets enforce transaction policies, multi role approvals, and operational constraints directly at the signing layer. This turns wallets into programmable governance infrastructure.
What is the role of RegTech in enterprise MPC wallet infrastructure?
RegTech integrations enable monitoring, compliance checks, reporting, and policy enforcement. This ensures MPC wallet operations align with regulatory and internal control requirements.
Is MPC suitable for enterprise scale transaction volume?
Yes. Enterprise MPC architectures are designed to support high frequency, high volume transaction flows with predictable performance and resilience.
Are MPC wallets compatible with multiple blockchains?
Most enterprise MPC wallet platforms are chain agnostic, supporting multiple blockchains through standardized signing and abstraction layers.
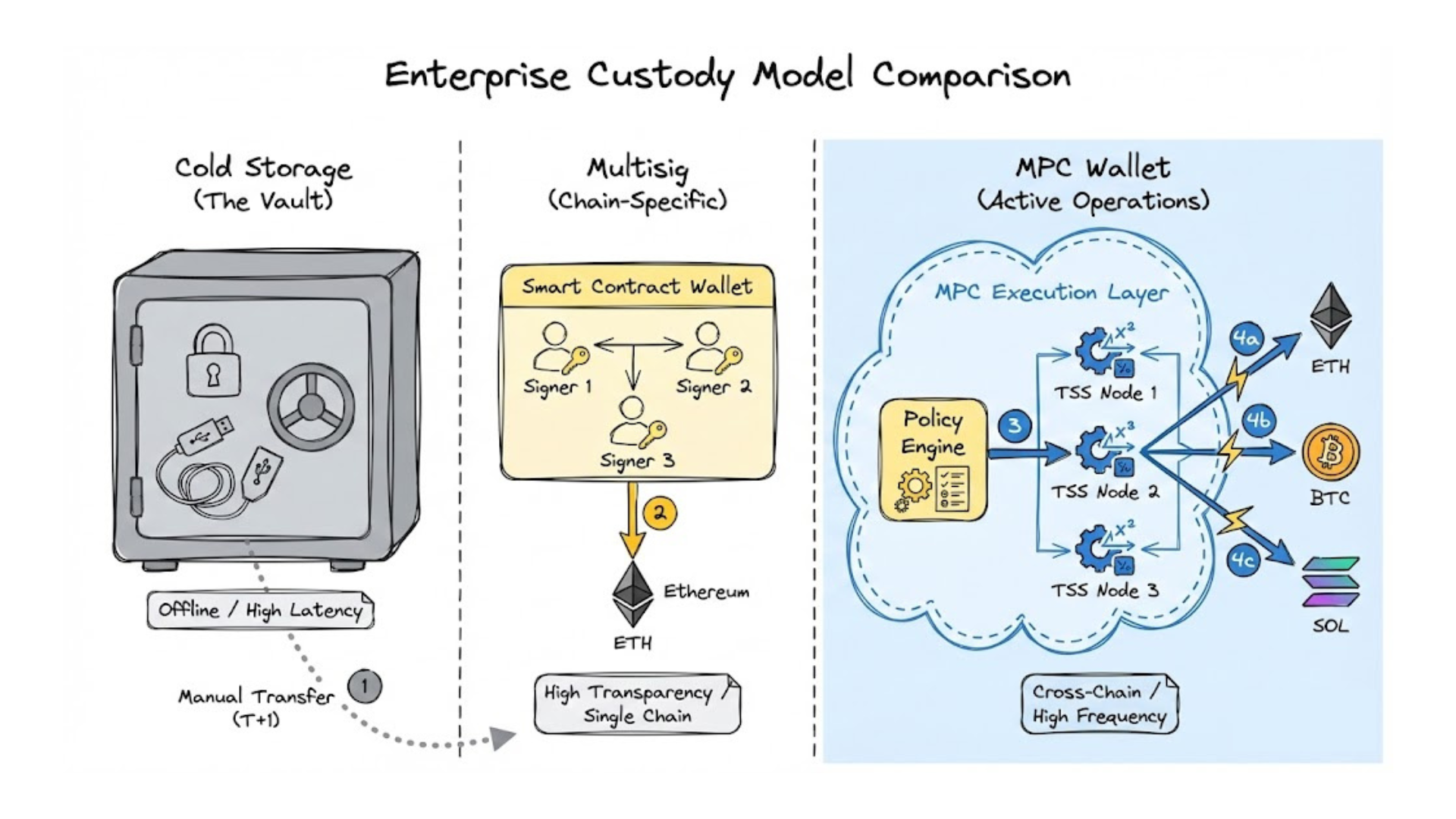
MPC vs Multisig vs Cold Storage: Which Custody Model Fits Enterprises?
Choosing a custody model is not a technical preference.
For enterprises, it is an operational and risk-management decision that directly affects compliance, cost, execution speed, and scalability.
Historically, multisig wallets and cold storage (HSM-based custody) were the default choices. By 2026, however, MPC wallets have emerged as the dominant model for production-grade systems operating across multiple chains and high transaction volumes.
High-Level Comparison for Decision Makers
| Dimension | MPC Wallet | Multisig Wallet | Cold Storage / HSM |
|---|---|---|---|
| Security model | Distributed cryptographic control | On-chain approvals | Centralized key isolation |
| Transaction speed | Near real-time | Slower due to on-chain execution | Slow, manual processes |
| Chain support | Chain-agnostic | Chain-specific | Chain-specific |
| Governance privacy | Off-chain, hidden | Visible on-chain | Internal only |
| Operational flexibility | Policy-driven | Contract-bound | Highly rigid |
| Scalability | High-frequency, automated flows | Limited | Very limited |
This comparison reflects a core reality:
Multisig and cold storage were designed for asset protection. MPC is designed for active operations.
When Multisig Still Makes Sense
Multisig wallets remain viable in narrow, well-defined scenarios, typically when:
- Operating on a single smart contract chain
- Managing simple DAO or community treasuries
- Prioritizing on-chain transparency over governance privacy
- Transaction frequency is low
However, multisig becomes increasingly difficult to manage when enterprises:
- Expand to multiple blockchains
- Require dynamic approval policies
- Need fast execution for payments and settlements
At that point, on-chain governance becomes an operational constraint rather than a benefit.
Read more: MPC vs. Multisig Wallets
Why Enterprises Are Moving Beyond Cold Storage Alone
Cold wallets and HSM-based custody excel at long-term asset protection, but they introduce friction for day-to-day operations.
Common limitations include:
- Manual approval workflows
- Delayed transaction execution
- Poor support for automated or programmatic payments
As a result, many enterprises now treat cold storage as a storage layer, not a transaction layer.
Cold storage protects reserves.
MPC enables execution.
Why MPC Is Becoming the Enterprise Default
Enterprises increasingly select MPC wallets when they require:
- Cross-chain treasury operations
- High-frequency or automated transactions
- Granular approval policies without redeploying contracts
- Private governance structures
- Seamless integration with existing backend systems
In practice, MPC allows enterprises to operate digital assets using the same control models found in traditional finance, while maintaining self-custody.
Is MPC safer than multisig for enterprises?
In most enterprise environments, yes. MPC reduces on chain exposure, keeps governance logic off chain, and supports dynamic approval policies without redeploying smart contracts. Multisig can be secure, but it becomes operationally rigid as transaction volume and organizational complexity increase.
Why do enterprises not rely on cold storage alone?
Cold storage is effective for long term asset protection, but it is not designed for frequent transactions, automated payments, or real time settlement flows. These limitations make it unsuitable as a primary execution layer for modern fintech and payment systems.
Can MPC replace both multisig and cold wallets?
In practice, MPC often replaces multisig for operational wallets, while cold storage is still used for deep reserves. Many enterprises use MPC for execution and cold storage strictly for long term holding.
Which custody model is best for cross chain operations?
MPC is the most practical choice for cross chain operations. Multisig and cold wallets are typically chain specific and difficult to coordinate across multiple networks.
Why Enterprises Are Standardizing on MPC Wallets
By 2026, enterprises are no longer adopting an MPC wallet for experimentation.
They are standardizing on MPC as core wallet infrastructure because it aligns with how modern organizations operate, scale, and manage risk.
This shift is driven by three practical business factors.
Operational Efficiency at Scale
Enterprise blockchain operations are no longer limited to manual transfers.
They increasingly involve programmatic payments, automated settlements, treasury rebalancing, and cross-border flows.
MPC wallets enable:
- Policy-based approvals instead of manual signing
- Automation without sacrificing internal control
- Faster execution compared to on-chain approval models
This allows finance and engineering teams to treat wallets as infrastructure components, not operational bottlenecks.
For a deeper breakdown of how MPC supports production-grade systems, Fystack explains why MPC has become critical infrastructure for enterprise Web3 security.
Risk Management and Internal Controls
Traditional private-key custody concentrates authority into a single technical or human point of failure.
MPC wallets introduce separation of duties by design:
- No single operator can move funds independently
- Internal approval logic is enforced cryptographically
- Insider risk is materially reduced
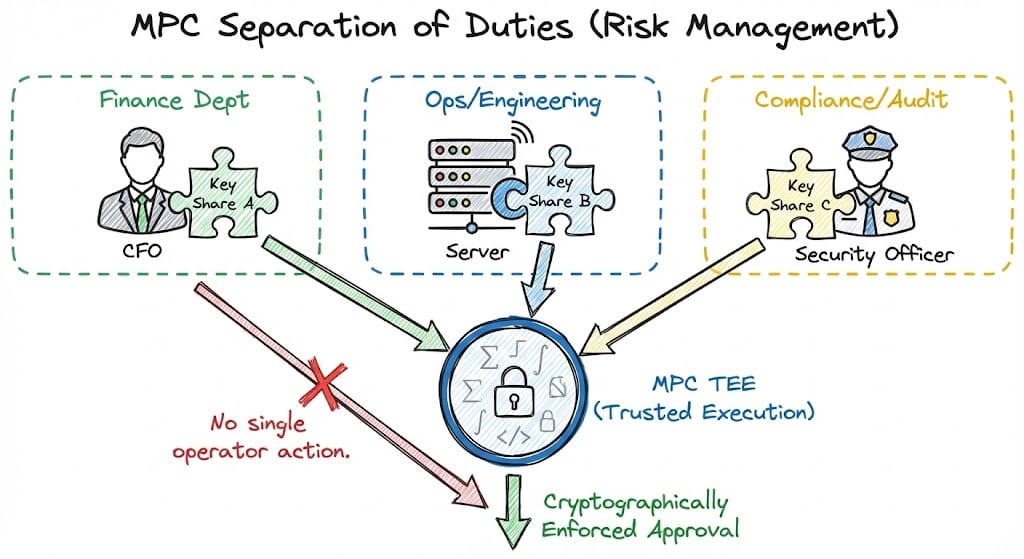
These controls closely mirror those used in traditional finance, making MPC wallets a natural fit for enterprises transitioning on-chain.
Compliance and Fintech Readiness
For fintech companies, custody is not only about security. It is also about regulatory alignment and operational clarity.
MPC wallets support:
- Clear audit trails
- Role-based access models
- Configurable approval thresholds
- Regional deployment for data sovereignty
This explains why MPC is increasingly adopted by regulated fintechs, payment providers, and tokenization platforms. This adoption pattern closely mirrors institutional custody workflows, where MPC wallets act as the core transaction and governance layer rather than a passive storage mechanism.
Fystack explores this transition in detail by outlining why fintech companies choose MPC wallets to go on-chain and how MPC aligns with compliance requirements.
From Tooling to Standard Infrastructure
The most important shift is conceptual.
Enterprises no longer view MPC wallets as:
- A niche cryptographic feature
- A developer-only tool
Instead, MPC wallets are now treated as:
- Core security infrastructure
- A prerequisite for scalable on-chain operations
- The default custody model for production systems
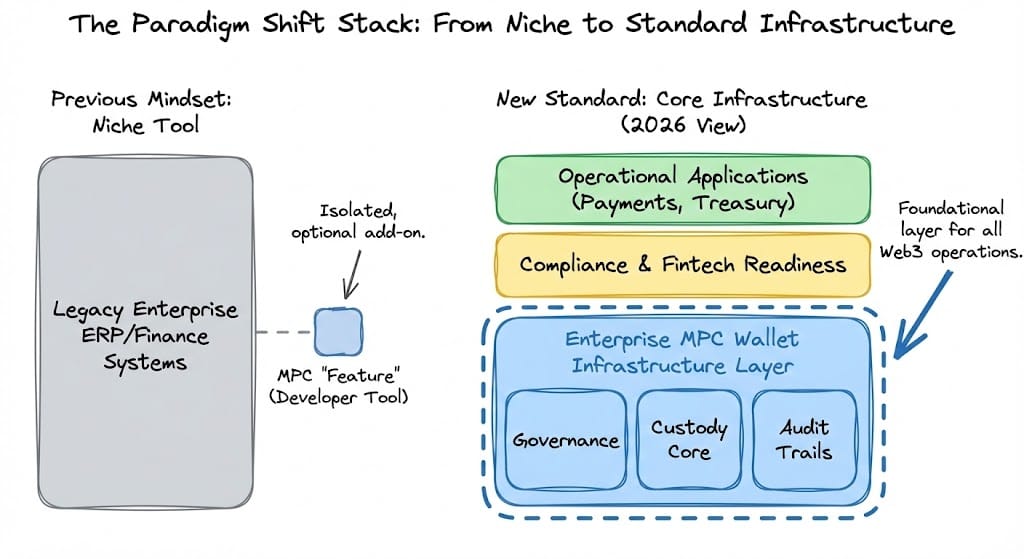
Why are enterprises moving away from single private keys?
Single key models do not support separation of duties, internal approval workflows, or recovery mechanisms required at enterprise scale. They concentrate both technical and operational risk into a single point of failure.
Is an MPC wallet suitable for high volume payment systems?
Yes. MPC wallets are widely used for automated, high frequency, and cross border payment flows because signing happens off chain and does not introduce on chain execution delays.
Do regulators accept MPC based custody models?
MPC aligns well with regulatory expectations around access control, auditability, and operational resilience, particularly when implemented in a self hosted or clearly defined governance model.
Is MPC only relevant for large enterprises?
No. Startups often adopt MPC wallets early to avoid costly architectural migrations later, especially as transaction volume, compliance requirements, and operational complexity increase.
Implementation Models: SaaS vs Self-Hosted MPC Wallets
Once an organization decides to adopt an MPC wallet, the next critical question is no longer about cryptography.
It is about implementation model.
By 2026, enterprises typically choose between two approaches:
- SaaS-based MPC custody
- Self-hosted MPC wallet infrastructure
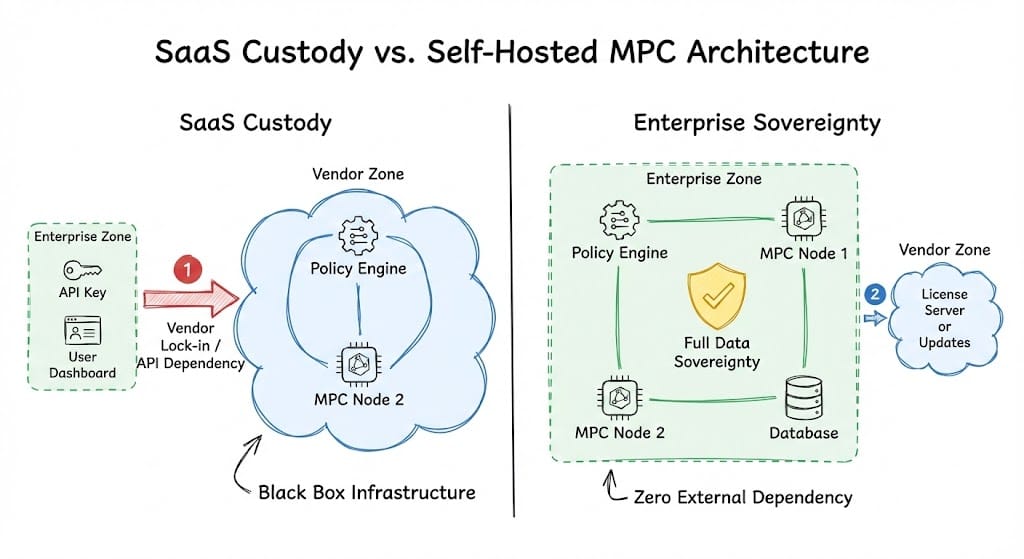
Each model carries materially different implications for control, compliance, and long-term risk.
The SaaS Model: Speed at the Cost of Control
SaaS MPC providers abstract away infrastructure complexity and offer fast deployment.
This model is often attractive for teams optimizing for time-to-market.
However, SaaS-based MPC wallets introduce structural constraints that become increasingly visible at scale:
- Vendor lock-in through proprietary signing logic and APIs
- Custodial risk when key shares are controlled by third parties
- Regulatory exposure, as assets may be classified under third-party custody
- Cost models tied to AUM or transaction volume, which scale poorly
As transaction volume and compliance requirements grow, these constraints often shift from convenience to blocker.
For a detailed breakdown of this trade-off, Fystack provides a direct comparison between SaaS custody and self-hosted MPC models, focusing on operational and regulatory impact.
The Self-Hosted Model: Enterprise-Grade Sovereignty
Self-hosted MPC wallets place full control of key shares, infrastructure, and policies inside the organization’s own environment.
This model enables:
- True enterprise-level self-custody
- Data sovereignty across regions and jurisdictions
- Custom security architectures aligned with internal risk frameworks
- Clear exit paths without dependency on a single vendor
For enterprises operating in regulated or cross-border contexts, self-hosted MPC is increasingly viewed as the only sustainable long-term option.
Fystack details this approach and its implications when explaining why ownership matters in MPC wallet infrastructure.
The Hybrid Approach: A Growing 2026 Trend
Many organizations now adopt a hybrid MPC model, combining:
- Self-hosted key shares for sovereignty and compliance
- Select managed services for monitoring, orchestration, or recovery
This approach balances control with operational efficiency and is increasingly common among fintechs scaling from startup to enterprise.
Regulatory and Legal Considerations
From a legal and compliance standpoint, custody architecture directly affects:
- Asset ownership classification
- Licensing requirements
- Liability in the event of incidents
These considerations are becoming more pronounced as regulatory expectations for Web3 fintechs mature across jurisdictions.
Self-hosted MPC wallets allow enterprises to retain clear ownership of cryptographic control, reducing ambiguity around third-party custodianship and regulatory exposure.
Is SaaS MPC considered custodial?
In many jurisdictions, yes. If a third party controls key shares or signing policies, the setup may be classified as custodial, with corresponding regulatory and compliance obligations.
Why do enterprises avoid vendor lock in for MPC wallets?
Wallet infrastructure sits at the core of asset control. Vendor lock in increases operational risk, limits architectural flexibility, and complicates long term compliance and exit strategies.
Is self hosted MPC only suitable for large enterprises?
No. Many startups adopt self hosted MPC early to avoid costly migrations later, especially as transaction volume, compliance requirements, and system complexity increase.
Can teams start with SaaS MPC and migrate later?
Migration is possible, but often complex. Differences in key management, signing logic, and policy enforcement make transitions costly. As a result, many teams now design for self hosted MPC from the outset.
Conclusion
By 2026, MPC wallets are no longer an emerging security model.
They have become the default custody architecture for enterprises operating on-chain.
For organizations managing real capital, regulated flows, and high transaction volume, MPC wallets offer a balance between security, operational control, and scalability that traditional private-key models cannot provide.
As blockchain infrastructure continues to professionalize, MPC wallets are not a competitive advantage - they are a baseline requirement.
At Fystack, we are building the infrastructure to help enterprises answer that question with confidence.
If you care about security, compliance, and reliability in Web3 operations:
👉 Try Fystack today: https://app.fystack.io
👉 Join our Telegram community for web3 security updates, engineering insights & product updates: https://t.me/+9AtC0z8sS79iZjFl