MPC Wallets: The Critical Infrastructure for Enterprise-Grade Web3 Security
Ted Nguyen
Author
BD & Growth @Fystack

As the number of crypto hacks increases, fintech, web3 teams are compelled to re-evaluate their approach to managing digital asset keys.
This article outlines how MPC wallets provide enterprise-grade custody solutions that extend beyond conventional models and assist teams in maintaining security in an ever-changing environment.
Why MPC Technology Matters
To understand the importance of MPC technology, we must first acknowledge the harsh truth about crypto hacks.
In 2024, breaches in the crypto sector resulted in a loss of $2.2 billion, with private key compromises representing 43.8% of the stolen funds.
It’s even worse in 2025. By mid-2025, Chainalysis indicated that nearly $2.17 billion had been hacked just in the first half of the year.

Crypto exchanges continue to be at the very core of this crisis. Publicly reported hacks from exchanges such as Phemex ($85M), Bybit ($1.34B), Nobitex ($85M), and others have wiped off billions from users and institutions.
Our article, “2025: The Year Crypto Exchanges Got Hacked — And Why Exchange SecOps Is Failing Us,” provides an in-depth exploration of this topic.
At the core of many of these failures is a familiar pattern:
private keys are still centralized and controlled by a single operational domain.
That design turns one key, one machine, or one compromised operator into a single catastrophic point of failure. Lose the key, leak it, or sign the wrong transaction once, and funds are gone.
As we approach 2026, it is alarming that many exchanges still rely on this outdated security model.
Importantly, a significant portion of these hacks could likely have been prevented if MPC had been deployed correctly, not just as a buzzword. MPC alone is not enough. The real protection comes from MPC combined with enforceable guardrails, such as:
- Policy-based signing (limits, whitelists, velocity controls)
- Transaction simulation and risk scoring before approval
- Segregation between hot, warm, and treasury signing roles
- Independent quorum participants across infrastructure and teams
- Auditability and deterministic approval flows
When implemented properly, MPC removes the single point of key compromise while preserving usability, regulatory control, and operational speed.
Fintech teams should understand MPC technology, as it removes the single point of failure, and maintains usability and compliance.
Let’s examine what this technology really is and how it could possibly become your best security options.
What is an MPC Wallet?
In institutional finance, relying on a standard private key is like giving a single employee the only code to the bank vault. It creates a massive Single Point of Failure.
As transaction volume scales, you cannot rely on trust alone. You need a system where moving funds requires a consensus of approvals, ensuring that no single compromised device or employee can drain the treasury.
MPC (Multi-Party Computation) is a cryptographic technology that splits a private key into multiple independent shares stored across different devices or locations. At no point is the private key ever fully reconstructed. This eliminates single points of failure and significantly improves security.
When a transaction requires approval, a set number of shares work together using a secure protocol to create a valid digital signature without revealing any individual key share or the complete key.
This method protects against key loss, insider threats, and device issues while allowing flexible access controls needed for secure digital asset management.
Next, we’ll explore how MPC works technically, focusing on distributed key generation and signing processes.
How MPC Wallets Work
MPC wallets are built on threshold cryptography, which combines Threshold Signature Schemes (TSS) and Distributed Key Generation (DKG).
DKG is used to create key shares without ever forming a full private key, while TSS is used to produce signatures collaboratively using those shares.
Threshold Signature Scheme (TSS)
Threshold Signature Scheme (TSS) TSS is the cryptographic mechanism that powers the signing process. Instead of reconstructing a private key to sign a transaction (which creates a single point of failure), TSS allows the participants to use their individual shares to collectively compute a valid signature.
This architecture enables programmable corporate governance. You can define 'M-of-N' quorum rules (e.g., 2 out of 3 must approve) directly into the cryptographic layer.
Beyond security, this ensures operational resilience: if a device is lost or an executive is unavailable, the organization retains access to funds through the remaining key shares, preventing liquidity gridlock.
Before threshold signing can happen, the key shares need a trusted way to be generated and distributed securely across participants. That’s where Distributed Key Generation (DKG) comes in.
Distributed Key Generation (DKG)
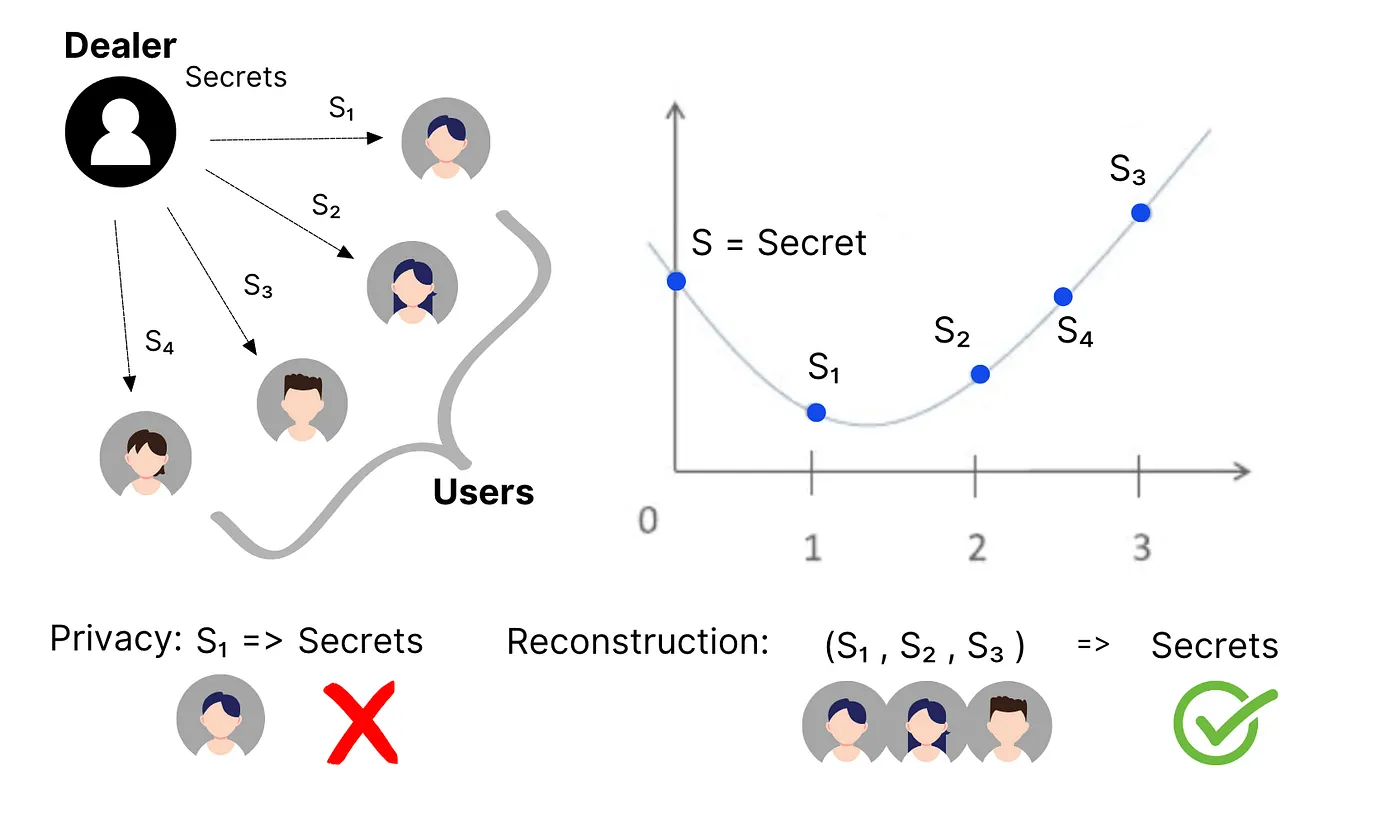
DKG is a key-creation mechanism that ensures the “original key” never exists in any single location. Instead of generating a private key first and then splitting it, the system creates the “key shares” from the start and distributes them to multiple parties.
This approach is based on Adi Shamir’s secret-sharing model: a secret is divided into several parts, and only when enough parts are combined can the original secret be reconstructed; with fewer parts, the holder gains no meaningful information.
In MPC wallets, DKG allows several participants to create these shares together. Participants create random secrets and share cryptographic proofs, which allows the group to form linked key shares without disclosing the full key.
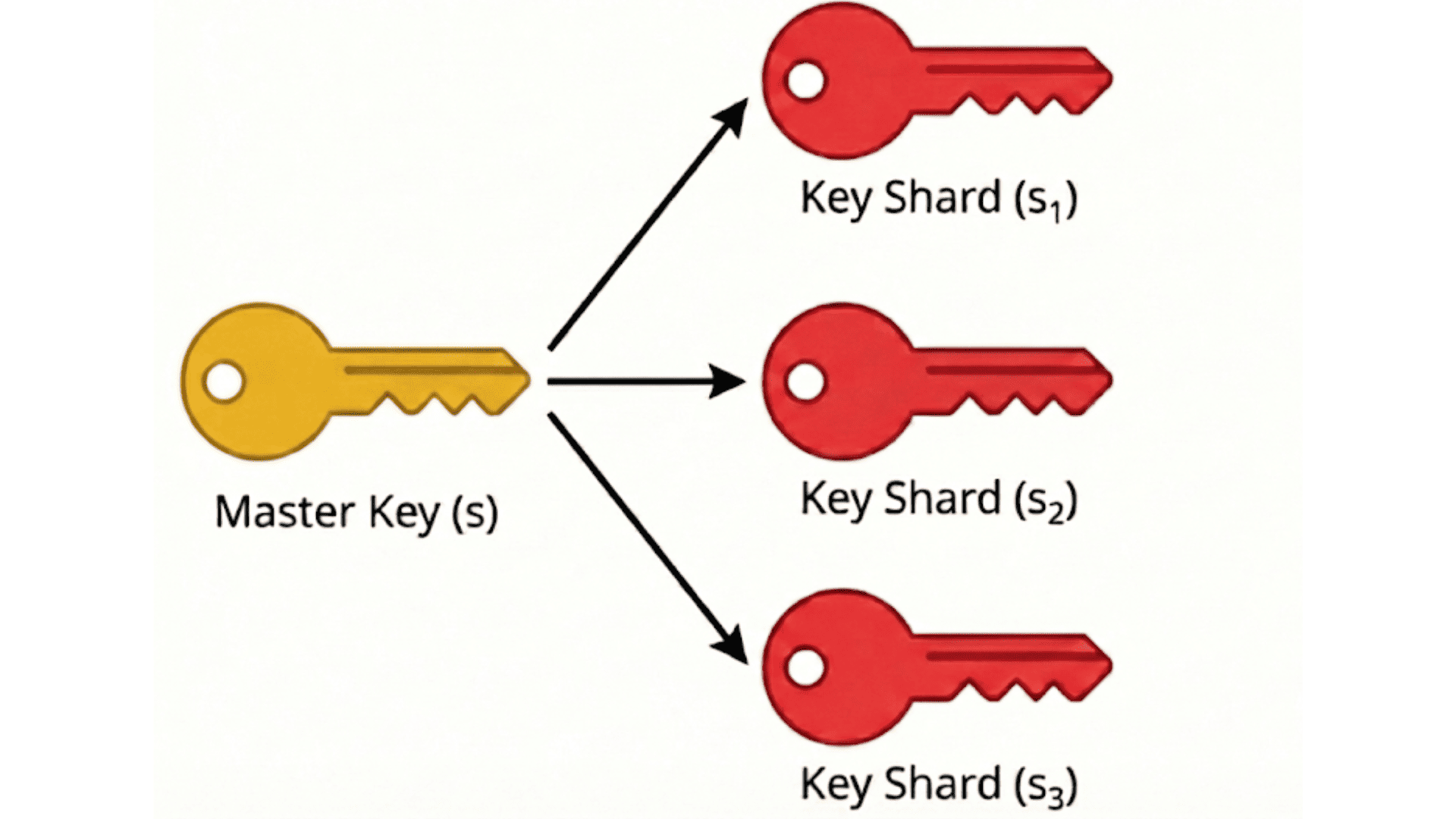
This process securely generates and distributes shares, supports configurable thresholds and enables recovery without modifying the public key or revealing secrets.
The Complete MPC Wallet Workflow
In a standard multisig setup, there is no shared private key. Instead, multiple independent private keys exist, each controlled by a different signer, and a smart contract enforces an M-of-N authorization policy.
With MPC wallet infrastructure, a single logical private key exists, but it is never reconstructed in full. The key is cryptographically split into multiple shares, distributed across independent parties or systems. Signing is performed collaboratively, and no participant ever holds the complete key material at any point.
Understanding the MPC wallet process helps teams understand its role in digital asset custody, compliance, and operations.
Here is the step-by-step workflow of how a transaction is secured and executed:
Phase 1: Setup & Key Generation (DKG)
Before any transaction occurs, the wallet must be initialized using Distributed Key Generation (DKG).
User’s Device, Custodian’s Server, and a Backup Device engage in a secure protocol. They exchange mathematical commitments to generate their own unique Key Shares and a common Public Key.
The Result:
Share 1: Stored securely on the user’s mobile device (Secure Enclave).
Share 2: Stored in custodian’s infrastructure.
Share 3: Offline backup (held by the user for recovery).
At no point during this phase is the full private key constructed or visible to any party.
Phase 2: The Transaction Request & Policy Engine
The user initiates a transaction (e.g., "Send 100 USDC") via the client app.
Before participating in signing, the request must pass through our Policy Engine. The system validates:
1/ User Rights: Is this user authorized to initiate this transfer?
2/ Spending Limits: Does this exceed the daily/weekly cap?
3/ Whitelists: Is the destination address verified or suspicious?
If any check fails, the server aborts immediately. If passed, the process moves to the signing phase.
Phase 3: Threshold Signing
Once the policy is validated, the User Device (Share 1) and Custodian Server (Share 2) begin the Threshold Signature Scheme (TSS) protocol.
To minimize latency, both parties can pre-generate random values (nonces) needed for the signature (offline pre-computation). Then, the devices exchange mathematical values derived from their Key Shares and the transaction message (online communication). And the Custodian Server combines these partial calculations to produce a final, valid blockchain signature.
Again, even during signing, the Key Shares are never merged, and the full Private Key is never reconstructed.
Phase 4: On-Chain Execution
The completed signature is attached to the transaction and broadcast to the blockchain network (Solana/Ethereum). Validators verify the signature against the wallet’s Public Key and execute the transfer just as they would for a standard single-key wallet.

The Evolution of MPC Wallets
The global Multi-Party Computation (MPC) market is exploding. It stood near $888 million in 2024 and is projected to reach roughly $2.72 billion by 2034. This massive growth confirms that MPC has become the backbone of modern digital asset security.
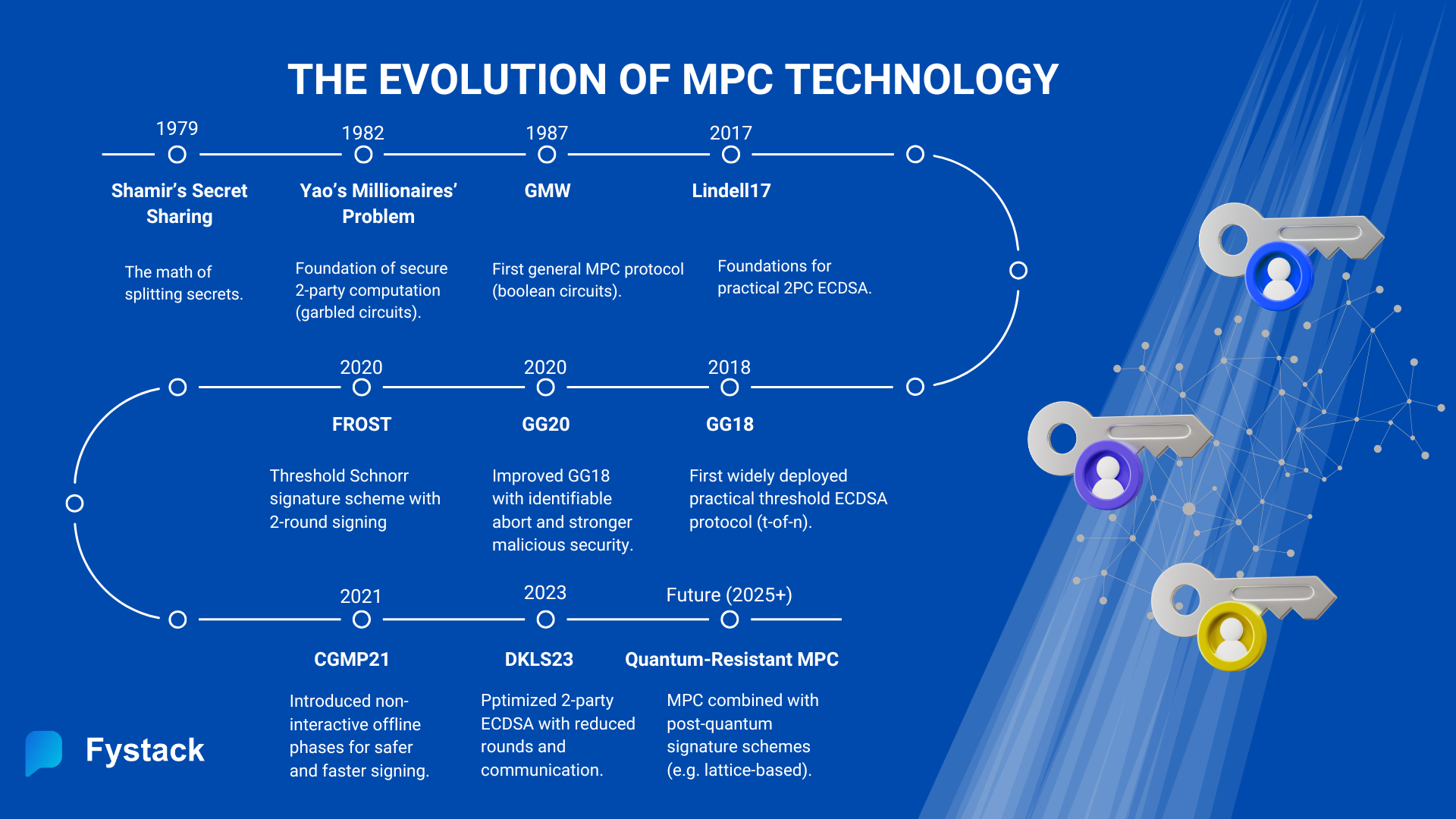
But this technology didn't just appear overnight. To understand why it is dominating the market today, we need to look back at its transformation, which began in the 1980s.
The Theoretical Foundation (1980s)
While Shamir’s Secret Sharing (1979) gave us the math to split keys, it was Andrew Yao (1982) who proved we could actually use them. He posed a simple question: How can two millionaires determine who is richer without revealing their exact net worth to each other?
Soon after, the GMW Protocol (Goldreich-Micali-Wigderson, 1987) generalized this concept, proving that any function could be computed securely by multiple parties, not just two. For decades, however, these breakthroughs remained largely theoretical and far too slow for real-world products.
The Blockchain Catalyst (2018)
The explosive growth of cryptocurrency created a desperate need for better security. Single private keys were too risky, and traditional multisig was difficult to scale across different blockchains.
In 2017, Lindell17 provided a crucial bridge. It introduced a fast protocol for 2-party ECDSA signing, enabling the first wave of client-server crypto wallets. However, true decentralized governance required more than two parties.
In 2018, the pressure led to a threshold breakthrough. GG18 (Gennaro & Goldfeder) became the first practical threshold protocol for ECDSA (Bitcoin/Ethereum). While technically revolutionary, it was still slow, requiring 9 rounds of back-and-forth communication to generate just one signature.
The Revolution (2020 – Present)
The last few years have been defined by a race to make MPC faster, safer and more scalable. In 2020, Gennaro and Goldfeder updated their protocol (GG20) to reduce the communication steps and add better security checks to detect bad actors. Then, CGMP21 emerged as the robust standard for institutions, offering a non-interactive preprocessing phase.
The biggest leap in speed came with Oblivious Transfer (OT) based protocols like DKLS23. These innovations optimized the process down to minimal communication rounds (milliseconds latency).
However, as quantum computing advances, traditional cryptographic algorithms (like ECDSA and RSA) face an existential threat from Shor’s algorithm.
The future of MPC is Quantum Resistance. The next generation of protocols will not just be faster; they will be built on post-quantum cryptography (PQC). This evolution ensures that MPC wallets remain secure not just against today’s hackers, but against the supercomputers of tomorrow.
(Read more: Why Fintech Companies Should Choose MPC Wallets to Go On-Chain)
A Complete Comparison Between MPC Vs. Other Wallet Architectures
Choosing a wallet infrastructure isn't about personal preference. You are choosing your trade-offs between security, convenience, cost, and privacy.
To help you navigate this, we’ve broken down how MPC compares to every major alternative on the market.
MPC vs. Hardware Wallets
Hardware wallets (like Ledger and Trezor) isolate the complete private key within a secure element, requiring physical access to the device for every transaction. While this eliminates network-based attacks, it introduces a single point of failure: if the device is lost or damaged, access is lost.
MPC wallets, by contrast, ensure no complete key exists in any single location. They offer built-in redundancy through distributed shares and can sign transactions from multiple devices. The trade-off is the requirement for network coordination between parties and constant connectivity.
MPC vs. Multisig Smart Contract Wallets
The distinction between MPC and multisig wallets (like Safe) often confuses newcomers, but they operate at fundamentally different layers.
Multisig wallets use smart contracts to enforce security. All signers, thresholds, and logic are visible on-chain. This transparency provides excellent auditability but can be a security risk for high-profile accounts (privacy leakage) and incurs higher gas fees due to on-chain verification.
MPC wallets operate at the cryptographic layer. The signing structure is kept completely private, generating standard transactions that are indistinguishable from single-signature users. This results in lower fees and better privacy. However, MPC cannot inherently implement the complex on-chain logic that smart contracts handle easily.
Read more: MPC Vs. Multi-sig Wallets
MPC vs. Traditional EOA Wallets
Traditional Externally Owned Accounts (EOAs) remain the simplest option: one private key controls everything. However, this makes them unsuitable for institutional or organizational use.
MPC technology evolved specifically to address this critical vulnerability while maintaining a user experience that feels similar to a standard EOA wallet.
When to Use MPC Wallets
MPC is a powerful tool, but it is not a universal solution. Understanding its specific strengths and limitations is key to deploying it effectively.
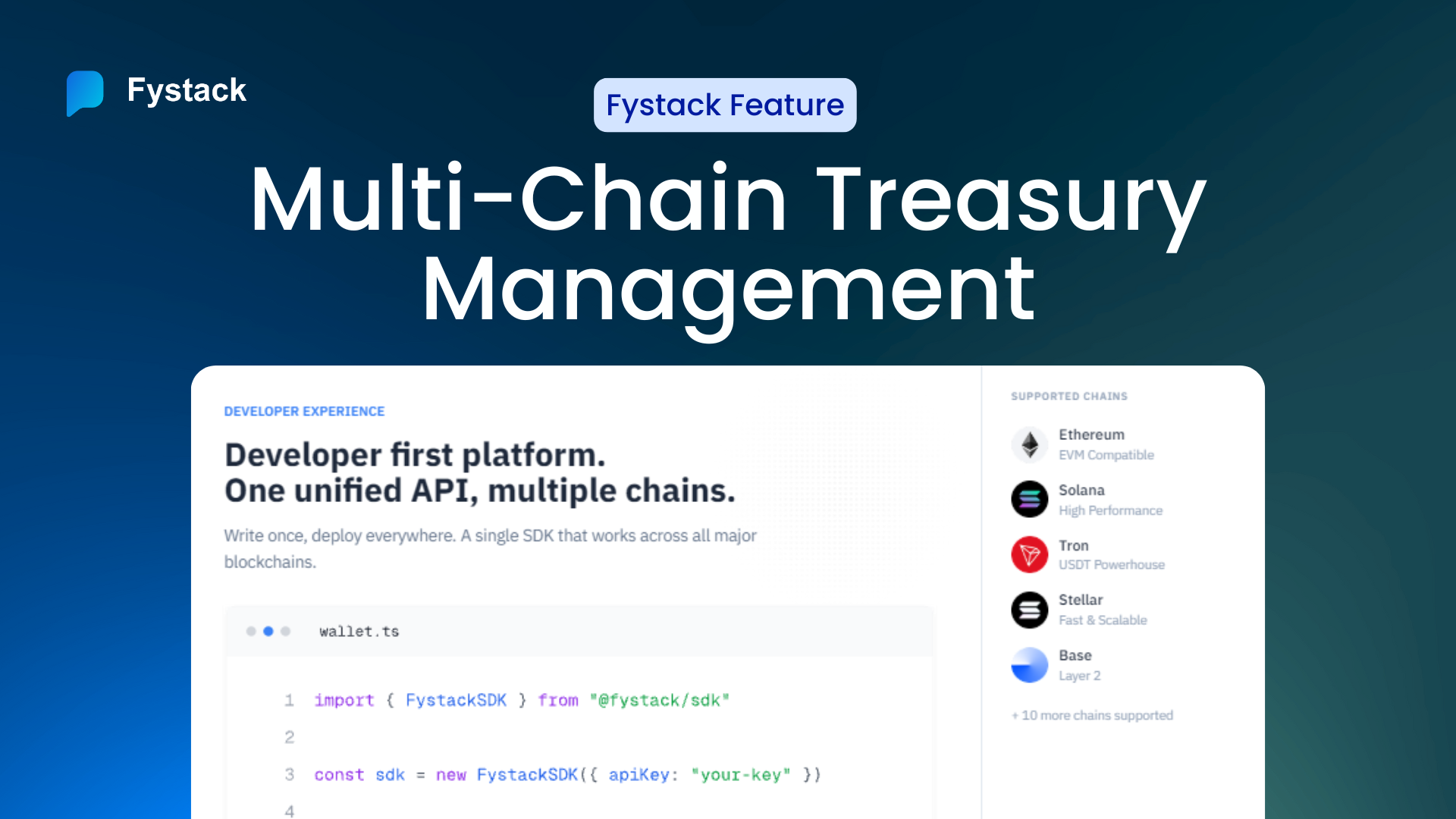
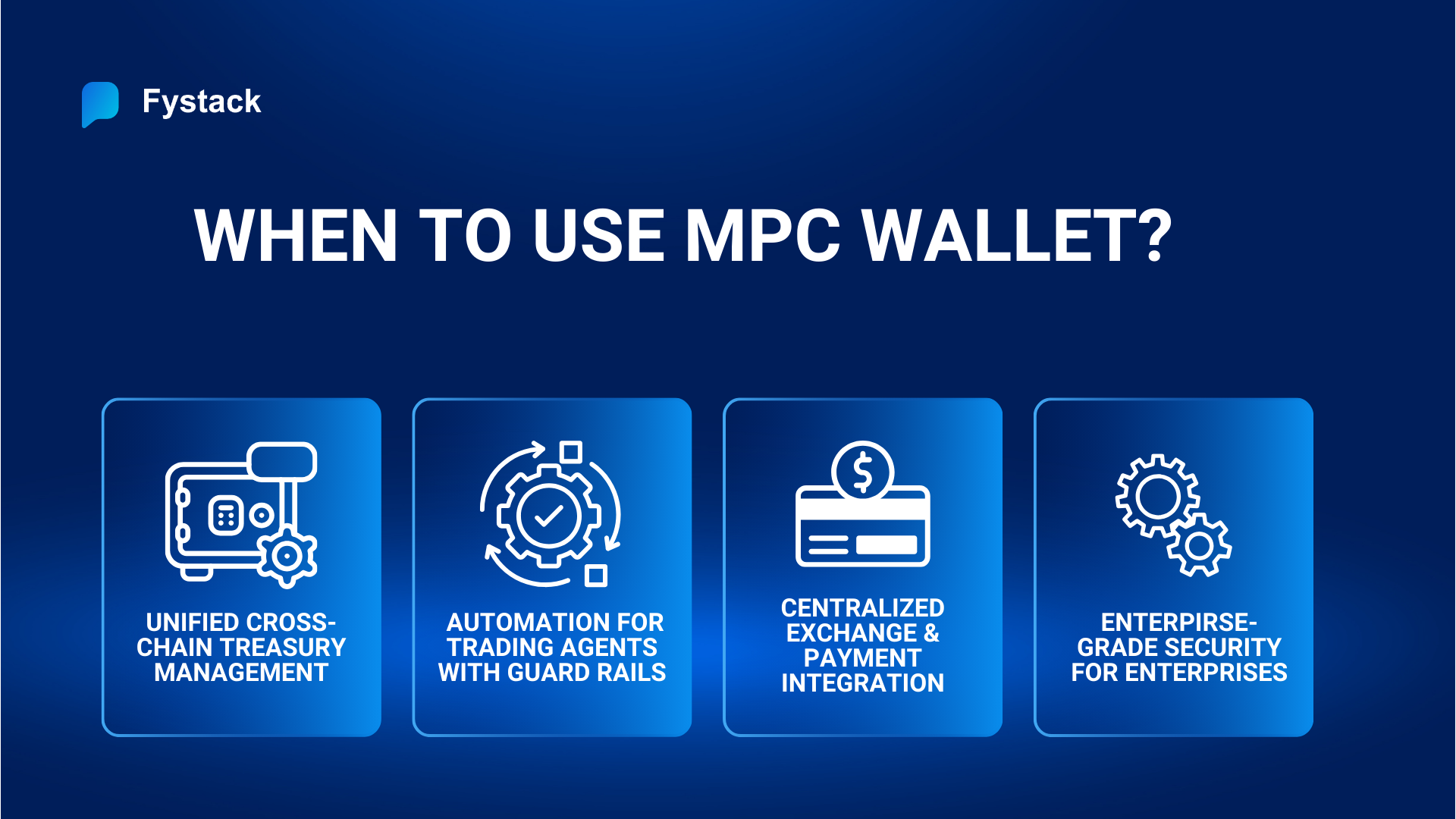
Unified Cross-Chain Treasury Management
The biggest headache for Web3 teams is fragmentation. You usually need a Gnosis Safe for Ethereum and Squads for Solana. Managing liquidity across five different chains means managing five different multisigs.
MPC solves this at the root. Because MPC operates off-chain using standard cryptographic curves (ECDSA/EdDSA), one MPC wallet architecture can govern assets across all chains.
Secure Automation for Trading Agents
We are entering the era of AI agents and trading bots. But giving a bot a private key is a massive security risk.
MPC allows you to build "Trading Agents with Guardrails."
The bot holds one key share, and the server holds another. You can program the server to only co-sign transactions that fit strict rules (e.g., "Only swap ETH to USDC" or "Never exceed $10k per trade").
You can run automated strategies with a "human-in-the-loop" approval layer or strict automated policy enforcement, eliminating the risk of a rogue bot draining the treasury.
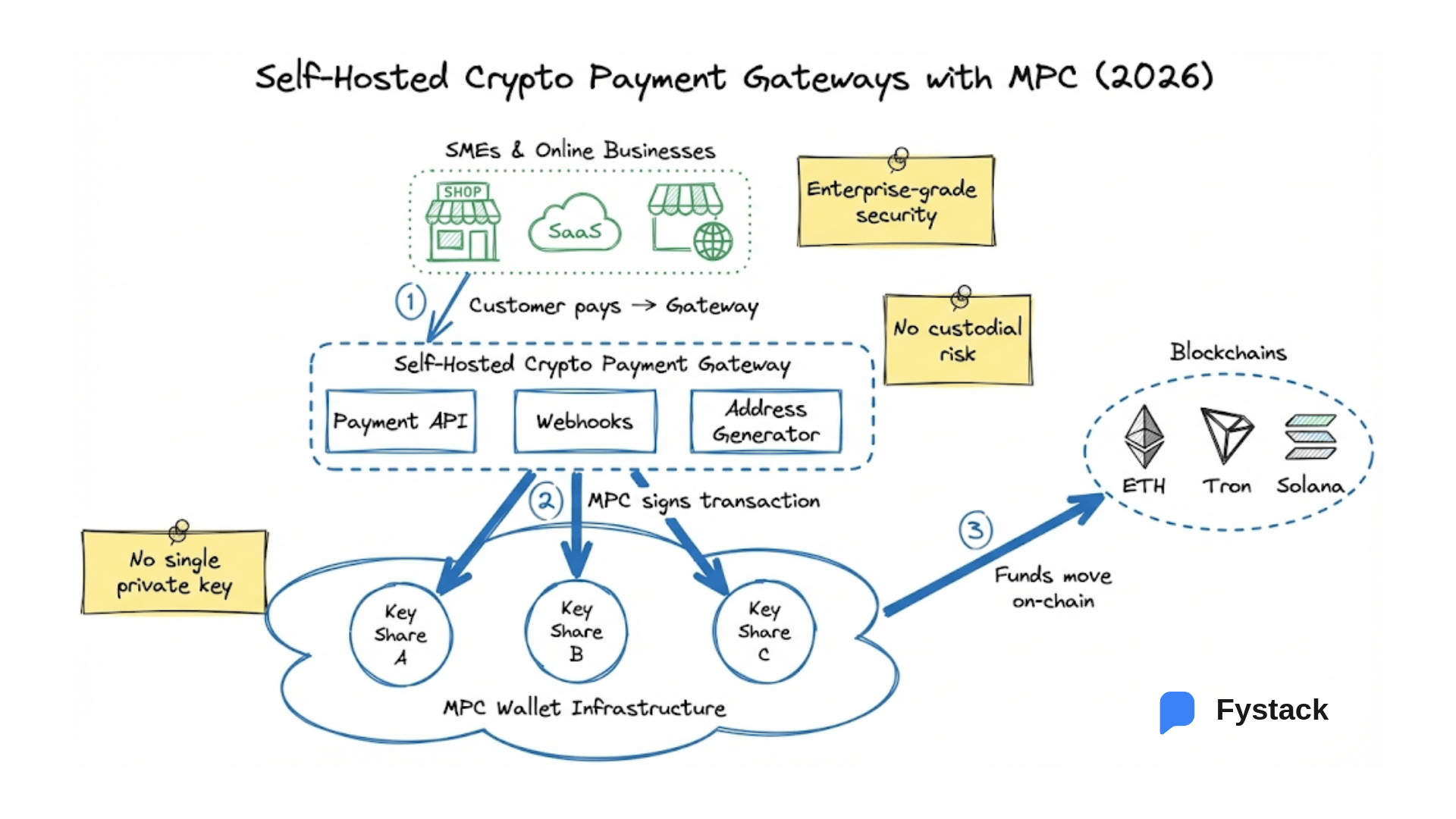
Centralized Exchange & Payment Integration
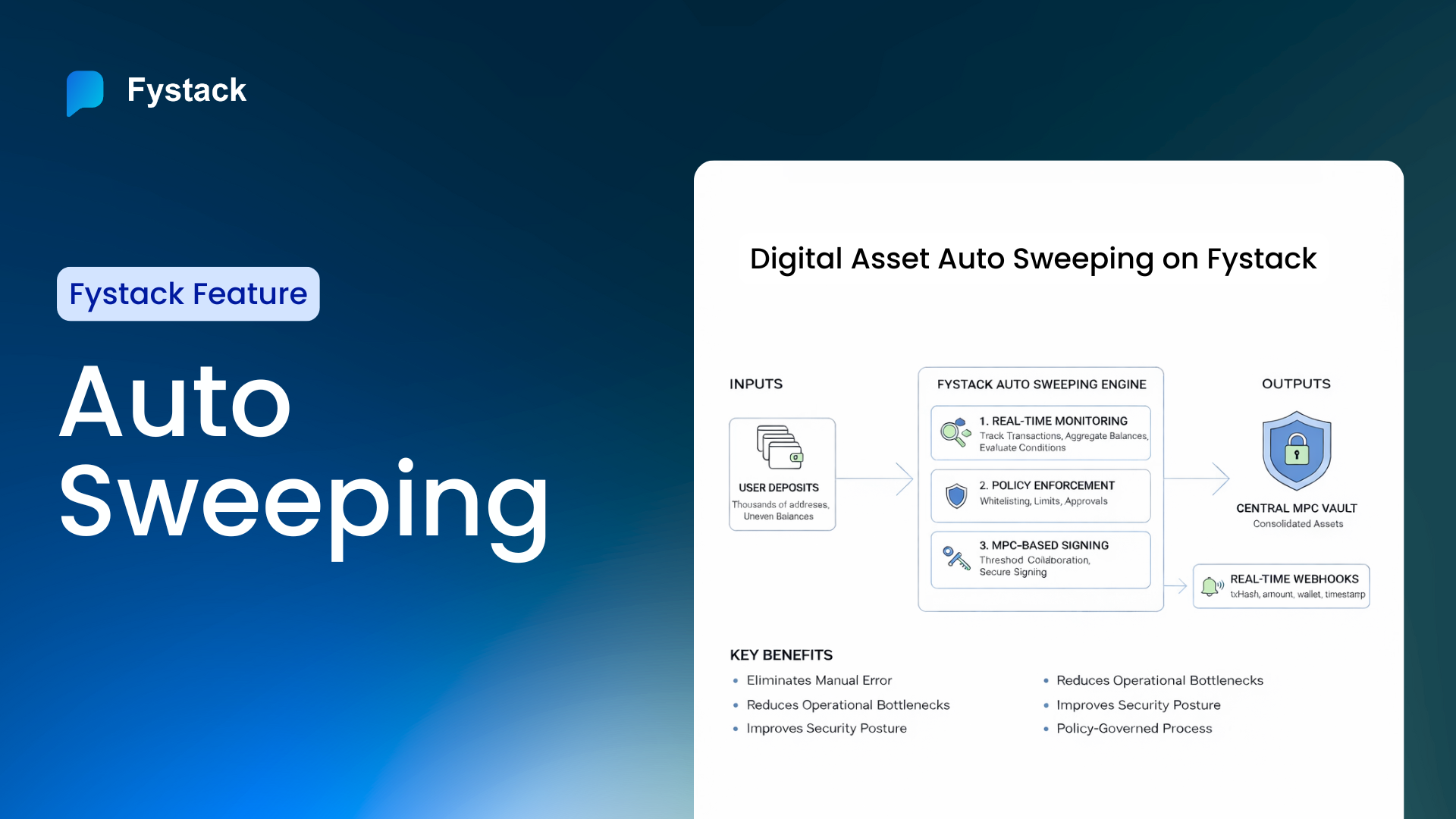
For crypto exchanges or payment processors, the challenge is consolidating funds. You might generate 100,000 deposit addresses for users. "Sweeping" those funds into a central cold wallet usually requires keeping a private key online (hot wallet) to sign the transfers, which is a prime target for hackers.
MPC enables secure, automated consolidation. You can program the MPC nodes to automatically sweep funds from deposit wallets to a central treasury without ever exposing a complete private key on a hot server. This allows for instant settlement processing while maintaining cold-storage-level security.
Maximum Control for Enterprises
For businesses that require absolute sovereignty over their data and keys, a SaaS solution isn't enough. At Fystack, we offer a self-hosted version that allows you to deploy the MPC infrastructure within your own environment. This gives you the automation of MPC with the complete control of a private setup.
Check out our MPCium documentation for deployment
When Other Solutions May Be Better
High-Frequency Trading (HFT)
HFT requires execution in microseconds. The communication overhead between MPC nodes (even milliseconds) is too slow for this specific niche. Traditional high-performance hot wallets or direct exchange connections are superior here.
Complex On-Chain Automation
Teams that need security logic embedded directly on-chain may benefit more from smart contract wallets. If an organization needs to batch transactions frequently, set up automatic gas payments, or enforce complex spending limits, smart contract wallets offer far more flexibility than MPC.
Decentralization and Self-control
For individuals who don't want to trust any server or software company, a physical hardware wallet that stays offline is the best choice for funds you rarely touch. While MPC is great for teams, a physical device is still the simplest way for a single person to keep money disconnected from the internet.
Performance & Operational Characteristics of MPC Technology
Beyond security architecture, the practical performance of a wallet determines its fit for high-growth businesses. MPC technology has evolved significantly, but understanding its real-world latency and throughput limits is critical for operational planning.
Latency: The Speed of Security
For most users, MPC feels instant. Modern software wallets using MPC sign transactions in 2-5 seconds under good network conditions, which is comparable to the 1-2 seconds it takes for a hardware wallet to sign once connected.
This is a massive improvement over traditional on-chain multisig setups, which can take minutes to coordinate and confirm on-chain. However, it’s important to note that MPC introduces a small computational overhead (typically 100-500ms) on top of standard network latency.
While this is negligible for standard transfers or DeFi interactions, it is a key reason why MPC is inappropriate for high-frequency trading (HFT) or MEV extraction strategies where microseconds matter.
The Geography Factor
MPC requires multiple devices to coordinate when signing a transaction, so their physical placement directly affects speed. When all devices are located in the same region, signatures happen quickly, usually within 1-2 seconds.
But if a company spreads devices across continents for higher resilience - for example, one in Tokyo, one in New York, and one in London - network latency naturally slows things down, pushing signing times to 3–10 seconds.
Because of this, most enterprises take a practical approach: devices that serve the same transaction flow are placed in the same region (e.g., an Asia cluster for Asia traffic, a Europe cluster for Europe traffic). This keeps signing fast, while additional clusters in other regions can still be deployed as backup for redundancy.
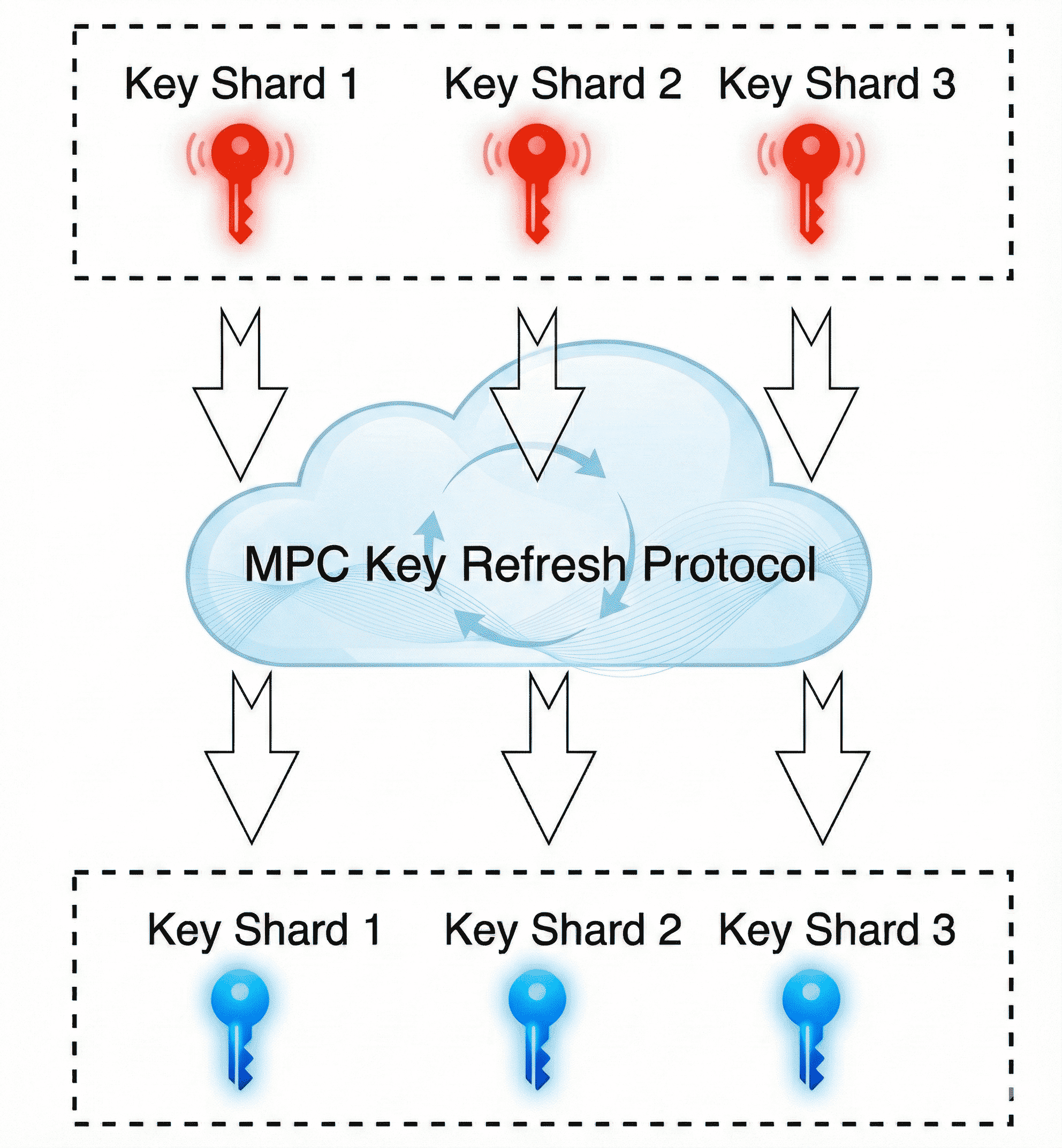
Key Rotation
One of MPC's most unique security features is "Key Rotation" or "Refresh." Unlike traditional wallets where changing a key means moving funds to a new address, MPC allows you to mathematically refresh the key shares without changing the public address. This can be done periodically or even automatically every few minutes.
For example, a hacker would need to compromise multiple shares simultaneously within that short timeframe to steal funds. Modern protocols have optimized this process from older, slower methods to cutting-edge standards that can refresh shares in a single round, making this dynamic defense practical for everyday use.
Myths and Misconceptions About MPC Wallets
As MPC becomes the industry standard, marketing teams tend to oversimplify it. Here are the 3 biggest myths we need to challenge.
MPC wallets are unhackable/have never been hacked
Many people assume MPC wallets are unhackable, but that is not entirely correct. MPC is a powerful cryptographic approach, yet risks still exist if the system is implemented incorrectly or operated insecurely.
The point here is, the MPC algorithms themselves (e.g., Lindell 21, CGGMP21) have never been mathematically broken. What we’ve seen in past incidents (such as Fireblocks BitForge in 2023 or misconfigured GG20 implementations) is that they were caused by implementation bugs, lack of audits, or compromised servers, not by flaws in the MPC technology itself.
Even though MPC is one of the strongest security models available for institutional and enterprise wallets, like any security technology, its effectiveness depends entirely on proper implementation, regular independent audits, and secure operational practices. When done correctly, MPC eliminates nearly all single-point private-key risks inherent in traditional wallets.
MPC is always better than multisig
As mentioned earlier, MPC and Multisig serve two different audiences. MPC is better in terms of cost and privacy while Multisig is better for transparency. With MPC, the blockchain sees a single signature. You can't tell who signed it just by looking on-chain.
However, if you need your signers and approval logic to be publicly visible (e.g., for a DAO’s public accountability), multisig is actually the better tool this time.
With MPC, I don't need backups
This is a recipe for disaster. If you lose access to your key shares (e.g., a server crash combined with a lost phone), you lose the funds.
Even with advanced technology like MPC, I don’t think we should be careless about the recovery plan. Backups are never a waste of time. Therefore, your businesses must have a plan for recovering key shares, whether through social recovery, offline backups, or a third-party emergency service.
Top MPC Wallet Providers 2026
The MPC landscape is competitive, with each provider optimizing for a different type of users. Here is a snapshot of the key players.
Fystack

While others offer closed SaaS platforms, Fystack is built for developers and businesses who demand sovereignty. Fystack provides an enterprise-grade, self-hosted MPC infrastructure that you deploy on your own servers with 100% control over your private keys and data with zero vendor lock-in.
With features like automated treasury sweeps, built-in compliance policies, and a developer-first API, Fystack is the "Stripe for Digital Asset Custody," allowing fintechs to launch secure crypto products in days, not months.
Learn more: How Fystack Compare to Other top MPC Wallet Platforms
Fireblocks
Fireblocks is the institutional giant, securing trillions in volume for banks and large custodians. Their platform is built on a "zero-trust" SaaS architecture and features a comprehensive compliance suite (SOC 2, ISO 27001) alongside a powerful policy engine.

Read more: Comparison between Fystack’s self-hosted model and Fireblocks’ SaaS platform
BitGo

BitGo bridges the gap between self-custody and regulated insurance. They offer a unique hybrid model, supporting both multisig and MPC wallets. Their platform is ideal for institutions that want an integrated solution for custody, staking, and trading under one regulated roof.
Qredo

Qredo pioneered decentralized MPC, removing the need for central hardware security modules (HSMs). Their network uses a distributed layer to secure keys, enabling cross-chain atomic swaps and fast settlements without centralized bottlenecks.
Fordefi

Fordefi is purpose-built for institutions actively trading in DeFi. Unlike standard custodians, their wallet integrates directly with dApps via a browser extension and simulates transactions to show users exactly what will happen before they sign.
Safeheron

Safeheron focuses on open-source transparency and the Asian market. They provide an institutional-grade MPC solution that clients can integrate via API or SDK, building trust by open-sourcing their core cryptographic libraries for verification.
Read more: Top Non-Custodial Solutions for Stablecoin Businesses
Future Trends for MPC Wallets
The wallet landscape is undergoing a massive shift. In 2025, the global crypto wallet market surged by over 32% to reach $19 billion, driven by mobile DeFi in APAC and institutional demand for self-custody.
The industry is moving towards Multi-Party Computation (MPC) as the bridge between Web2 usability and Web3 security.
Here is where the market is heading:
1. Seedless & Keyless UX
Wallets are becoming seedless and they create a recovery experience that feels like a standard Web2 login.
2. Policy Engine & Compliance Automation
Security is programmable. With new Policy-as-Code (PaC) engines, teams can now automate compliance to determine spending limits and approval workflows easily.
3. Self-hosted & Open-source MPC Wallet Infrastructure
Institutions are moving away from closed SaaS custodians. The trend is toward self-hosted, open-source MPC infrastructure that allows businesses to maintain full data sovereignty and meet strict regional compliance rules (like MiCA in EU or GENIUS Act in the US).
For a full breakdown of the latest updates from Top MPC Wallet Providers and the 5 Key Trends Defining 2026, read our full article: MPC Wallet News 2026: Latest Updates on Leading MPC Service Providers
Frequently Asked Questions (FAQs)
Is an MPC wallet non‑custodial or custodial?
It depends on who holds the key shares.
1/ Custodial: A vendor holds enough shares to sign transactions.
2/ Non-Custodial (Self-Hosted): You hold the shares on your own servers. You have full control.
3/ Shared/Collaborative: Shares are split (e.g., 1 for you, 1 for the vendor), requiring both to sign.
4/ Embedded: The wallet is integrated directly into an app via API.
Can MPC Wallets Support Multiple Blockchains?
Yes. Unlike multisig wallets (which are smart contracts specific to one chain), MPC operates at the cryptographic layer (off-chain). As long as the blockchain uses standard curves (like ECDSA for Bitcoin/ETH or EdDSA for Solana), one MPC wallet engine can manage assets across all of them simultaneously.
What happens if I lose one device/key share?
No worries. You don’t lose your funds. As long as you still have enough shares to meet the threshold (e.g., 2 out of 3), you can still sign transactions.
Are MPC Wallets Quantum-Resistant?
Not really. Most current MPC wallets rely on standard cryptography (ECDSA) which could theoretically be broken by a large-scale quantum computer in the future. However, the industry is already working on post-quantum MPC algorithms.
For now, the best defense is operational security: keeping shares distributed and rotating them frequently makes it exponentially harder for any computer (quantum or not) to compromise the wallet.
How do I choose the right MPC provider?
Ignore the marketing buzzwords and ask three questions:
1/ Do I get the source code? (If not, you are trusting a black box).
2/ Can I host it myself? (If not, you have data sovereignty risks).
3/ What is the signing protocol? (Look for modern standards like GG20 and newer, faster algorithms).
HSM vs. MPC: Which one is better?
It depends on your needs.
Since HSMs rely on physical hardware, they are great for storage but rigid. Scaling is limited by the device's capacity, and supporting a new chain often requires complex firmware updates. Plus, a broken device can create a single point of failure.
MPC, on the other hand, is software-based and blockchain-agnostic. This allows it to scale horizontally on demand to handle high transaction volumes and support new chains instantly. By splitting the private key into distributed shares that are never reconstructed, MPC eliminates single points of failure while offering superior agility.