Institutional Digital Asset Custody powered by MPC wallet: A Secure and Compliant Transaction Workflow
Thi Nguyen
Author
Founder

In the world of traditional finance, if you own a stock or a bond, you don't keep the physical certificate under your mattress. Instead, you rely on a trusted third party - a custodian bank to safeguard your assets, handle settlements, and manage the complex administrative work. This system is the bedrock of global finance, built on trust, security, and accountability.As digital assets like Bitcoin and Ethereum move from the fringes to the core of institutional portfolios, a similar, yet far more complex, need has emerged: institutional digital asset custodians. These are the quiet guardians, the essential infrastructure that allows major financial players from hedge funds and pension funds to banks and corporations to enter the crypto space with confidence.
Beyond the Private Key: The Custodian's True Role
The popular narrative around crypto often focuses on "being your own bank," but for institutions managing billions of dollars, that level of self-custody is a non-starter. It introduces unacceptable risks related to human error, internal fraud, and regulatory non-compliance.An institutional custodian does far more than just hold a private key. Their role is a triple mandate: Security, Governance, and Compliance.
1. Uncompromising Security: The Digital Vault
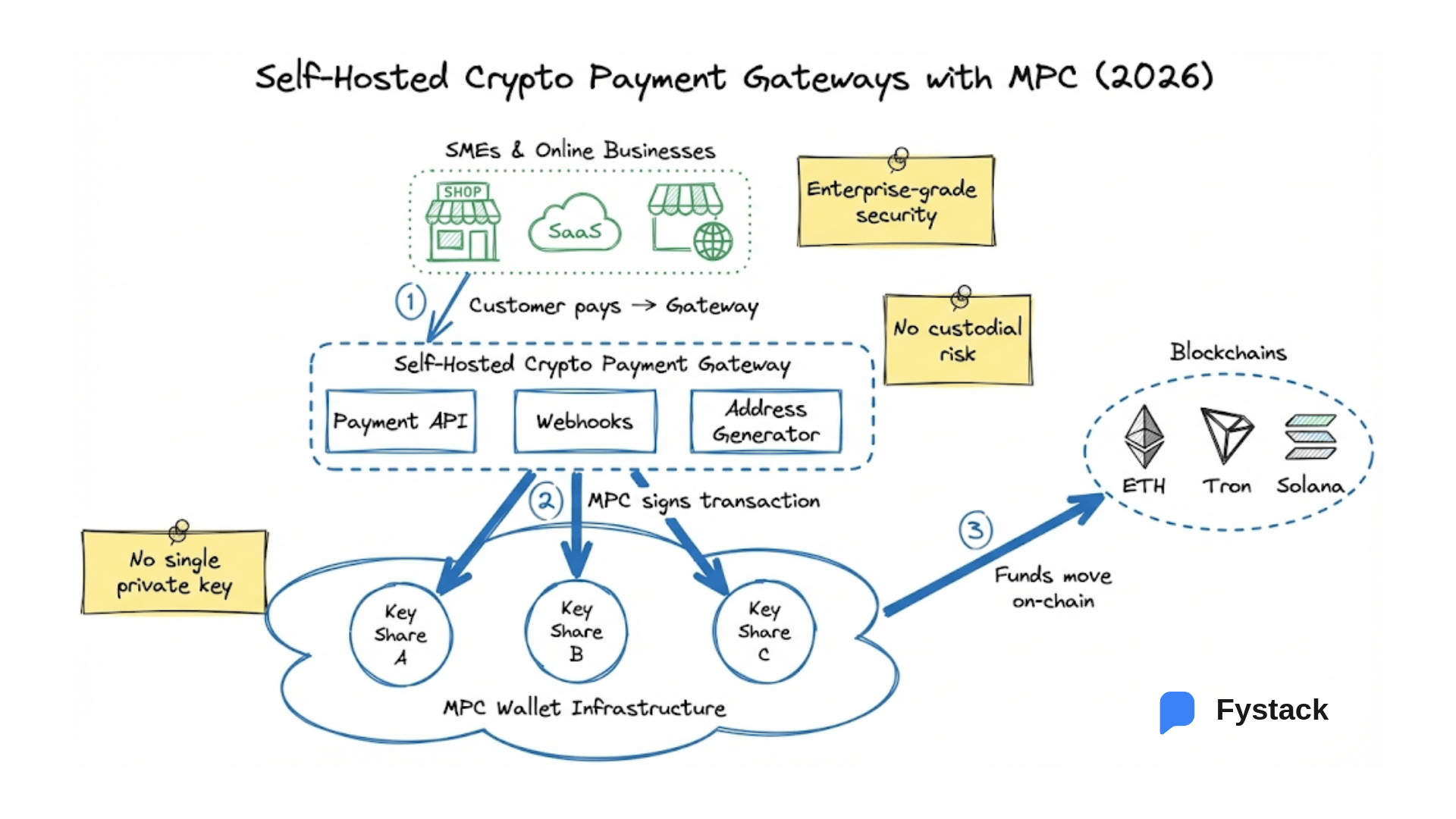
The biggest fear in digital asset management is the loss or theft of the private key, which is equivalent to losing the assets forever. Institutional custodians address this with state-of-the-art cryptographic technology.They have moved past the simple "hot wallet" (online) versus "cold wallet" (offline) debate. Today's leading custodians use Multi-Party Computation (MPC). Think of MPC not as a single key, but as a key that is instantly shattered into multiple pieces, or "shares," and distributed across different locations and parties. No single person or system ever holds the complete key. When a transaction needs to be signed, a quorum of MPC participants collaboratively performs the signing protocol. Each party contributes a partial cryptographic computation using its own key share, and the final signature is produced without any share ever being revealed or combined. A compromise of one system does not expose the private key or endanger the assets. Furthermore, they often use Trusted Execution Environments (TEE) and Hardware Security Modules (HSM) specialized, tamper-proof hardware to perform the most sensitive operations. This is the digital equivalent of a bank vault with biometric scanners, time-locks, and armed guards, all working in concert.
2. Corporate Governance: The Approval Quorum
For a major institution, a transaction is never a solo decision. It requires checks and balances. The custodian's platform is designed to enforce this internal governance structure.Imagine a high-value transfer. The system doesn't just ask for a password; it routes the request to an Approval Quorum - a group of senior executives, perhaps the CFO, CEO, and CTO. The platform enforces an m-of-n signature scheme, meaning that, for example, at least two out of the three executives must digitally approve the transaction before it can proceed. This separation of duties is crucial for internal controls and auditability, ensuring that no single individual can unilaterally move corporate funds.
3. Navigating the Regulatory Maze: Compliance as a Service
The regulatory landscape for digital assets is constantly evolving, and institutions must navigate complex rules like the Financial Action Task Force (FATF) guidelines. A custodian acts as a compliance partner, embedding these checks directly into the transaction workflow. Know Your Transaction (KYT): Before any funds are sent, the custodian's system automatically scans the recipient's blockchain address. This KYT check assesses the risk profile of the destination, flagging any addresses linked to sanctions, illicit activities, or high-risk entities. It’s like a real-time background check for every digital asset transfer. The Travel Rule: For transfers above a certain threshold, the custodian facilitates compliance with the Travel Rule, which requires Virtual Asset Service Providers (VASPs) to exchange identifying information about the sender and receiver. This is a critical step in preventing money laundering and is seamlessly handled by the custodian's integrated protocols .
The Value Proposition
Institutional custodians are not just a service, they are a prerequisite for the mass adoption of digital assets by the traditional financial world. They provide:
Feature | Benefit for Institutions |
MPC Technology | Eliminates the single point of failure; enhances security against internal and external threats. |
Approval Quorum | Enforces corporate governance and separation of duties; ensures transactions are auditable. |
Integrated KYT/Travel Rule | Automates complex regulatory compliance; reduces legal and operational risk. |
Secure Infrastructure (TEE/HSM) | Provides cryptographic assurance that keys are never exposed in plain text. |
By outsourcing the complexity of key management, security engineering, and regulatory compliance to a specialized custodian, institutions can focus on what they do best: investing and innovation. They are the essential bridge, transforming the wild west of crypto into a secure, governed, and compliant frontier for global finance.
Institutional Custody With Full Data Sovereignty
At Fystack, we are building self-hosted institutional custody infrastructure, powered by MPC-based wallets, for organizations that require absolute control over their assets, data, and security posture.
Unlike custodial SaaS platforms, Fystack is designed for complete data sovereignty:
- You own the keys, policies, and infrastructure
MPC key shares are generated, stored, and used entirely within your environment. No external party ever holds, reconstructs, or has access to your private keys or signing material. - Full control over security architecture
Deploy MPC nodes in your own cloud, on-prem, or hybrid setup. Integrate TEEs, HSMs, air-gapped cold signing, and hardware authenticators according to your internal threat model. - Governance enforced at the protocol level
m-of-n approval quorums, role separation, transaction policies, and limits are enforced cryptographically, not by process or trust. - Compliance without data leakage
KYT, Travel Rule, and audit logs run within your controlled environment, ensuring regulatory compliance without exporting sensitive transaction or identity data to third parties. - No vendor lock-in
Open, auditable infrastructure that your security and compliance teams can inspect, extend, and operate long-term.
Fystack is built for exchanges, fintechs, funds, and enterprises that cannot compromise on data ownership, security control, or operational transparency.
If you are designing or re-architecting institutional custody and need sovereign control with institutional-grade security, let’s talk.
→ Build custody infrastructure that you fully own, fully control, and can confidently defend to auditors, regulators, and your board.