2025: The Year Crypto Exchanges Got Hacked - And Why Exchange SecOps Is Failing Us?
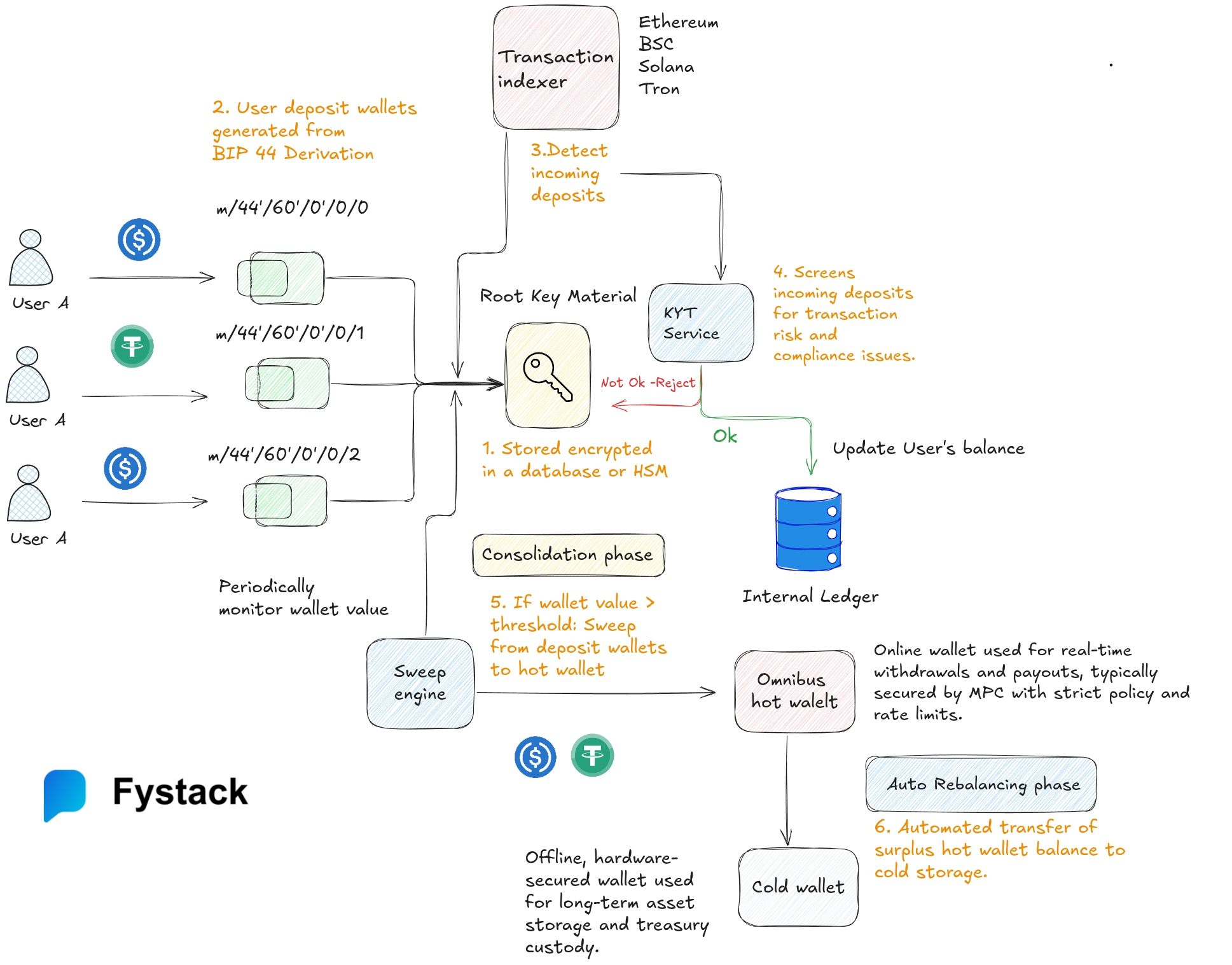
Thi Nguyen
Author
Founder

If you’ve been in crypto long enough, you’ve probably heard the same comforting line over and over:
“Your funds are safe. Exchanges have institutional-grade security.”
But 2025 has completely shattered that illusion.
We’re barely past Q4, and the world has already witnessed some of the worst exchange hacks and crypto-asset thefts in history. Amid them: an attack on South Korea’s largest exchange, which sent a stark warning to the industry. https://finance.yahoo.com/news/crypto-exchange-upbit-reports-36m-041439379.html
Yet 2025 has become one of the worst years in history for exchange hacks, with billions drained from platforms that millions trusted.
Below is a snapshot of just the major public breaches so far:
- Phemex: $85M (Jan 23, 2025)
- Bybit: $1.34B (Feb 21, 2025)
- Nobitex: $85M (Jun 18, 2025)
- BigONE: $27M (Jul 16, 2025)
- CoinDCX: $44.2M (Jul 19, 2025)
- WOOX: $14M (Jul 24, 2025)
- BtcTurk: $48M (Aug 14, 2025)
- Upbit: $36M (Nov 27, 2025)
Across these incidents, one pattern repeats over and over:
Weak SecOps → Hot/Cold Wallet Compromise → Catastrophic Losses
Despite sophisticated perimeter defenses, exchanges continue to rely on operational models that carry inherent centralization risk:
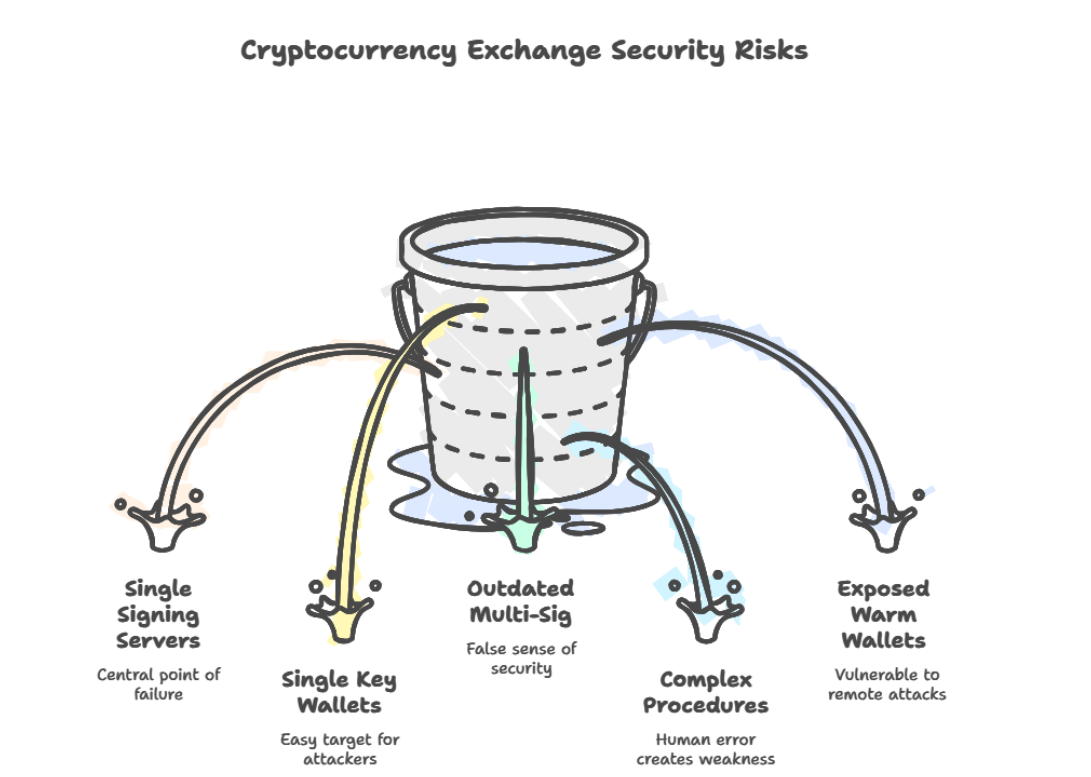
- Single signing servers
- Use single key wallet for critical operations
- Outdated multi-sig setups
- Complex operational procedures prone to human error
- Warm wallets exposed to internet-facing infrastructure
Once any part of the system is breached, a DevOps key, a server, a vendor dependency, a compromised signing workflow, attackers gain unrestricted access.
And when exchanges custody billions, even one misconfiguration can become a multi-hundred-million-dollar disaster.
Why Exchanges Keep Getting Hacked: A Structural Problem
Most exchanges still run on custody models designed 8–10 years ago:
1. Centralized control of keys
Even if keys are sharded or multi-sigged, the exchange itself ultimately holds full signing authority.
One point of failure = total loss.
2. Hot wallet exposure
To meet withdrawal demand, exchanges maintain warm or hot wallets, always online, always exposed.
Attackers only need one entry point. Defenders need zero mistakes.
3. Dependency on closed-source vendor tooling
2025 showed this clearly:
even “secure” wallet providers can be compromised.
If your custody stack is a black box, you inherit external risk you cannot verify or audit.
4. Human-driven security operations
Internal approvals, manual processes, privileged accounts…
Human error + access fatigue + social engineering = predictable breach vector.
Why Enterprise-grade self-Custody with MPC Matters More Than Ever
There is a simple truth emerging in 2025:
Assets aren’t safe just because they’re on a big exchange.
Assets are safe when you control the keys, not someone else.
Self-custody fundamentally changes the attack surface:
No centralized honeypot
There is no “exchange cold wallet” holding billions.
Each organisation controls its own keys or MPC shards.
No single point of failure
With MPC (multi-party computation), keys are never assembled in one place — not even during signing.
An attacker must breach multiple isolated systems simultaneously, which is orders of magnitude harder.
No dependency on opaque wallet vendors
Open-source stacks allow independent audits and cryptographic transparency.
Operational security becomes programmable
Policies such as withdrawal limits, address allowlists, velocity rules, 2-of-3 MPC signing, IP restrictions, enclave-backed shard protection, all enforced automatically.
Humans don’t decide security.
Systems do.
2025 Is the Wake-Up Call
Billions lost.
User funds wiped out.
Regulators tightening the screws.
Institutions demanding better infrastructure.
The market is sending a clear message:
Centralized custody is a systemic risk.
Decentralized, programmable, verifiable self-custody is the future.
If you’re an exchange, fintech, stablecoin issuer, payment processor, or Web3 business, depending on someone else’s keys puts your customers at risk, and your entire business at existential risk.
The Path Forward: MPC-Based Self-Custody for Every Business
Modern infrastructure makes it possible to adopt secure self-custody without needing a dedicated in-house cryptography team:
- MPC signing across multiple servers
- Policy engines for automated governance
- Hardware isolation (Nitro Enclaves, TPMs, TEEs)
- Invest in SecOps: https://fystack.io/blog/security-101-for-web3-startups
This is the direction the industry is moving, and 2025’s exchange hacks simply accelerate the shift.
Self-custody is no longer an “advanced option.”
It is the baseline for any business serious about security.
Stay Safe. Build Securely
Fystack is building enterprise-grade wallet infrastructure for teams, powered by MPC technology to eliminate single points of failure, prevent key theft, and protect organizations from modern attack vectors like video-meeting exploits and infostealers.
If you care about security, compliance, and reliability in Web3 operations:
👉 Try Fystack today: https://app.fystack.io
👉 Join our Telegram community for web3 security updates, engineering insights & product updates: https://t.me/+9AtC0z8sS79iZjFl