How Not to Get Hacked in Crypto (Part 1): Beware of Video Meetings
Thi Nguyen
Author
Founder
Crypto Victims Who Lost Millions to Deepfake Zoom Calls - 5 Case Studies
If you work in crypto, constant meetings are part of the job interviews, investor pitches, partnership calls, client demos. Unfortunately, this environment creates a perfect social-engineering honeypot for attackers. Hackers impersonate legitimate contacts and lure victims into what looks like a normal business meeting.
Even worse, many people have already fallen for these scams, losing significant amounts of crypto, sometimes entire wallets, company funds, or personal savings from a single compromised call.
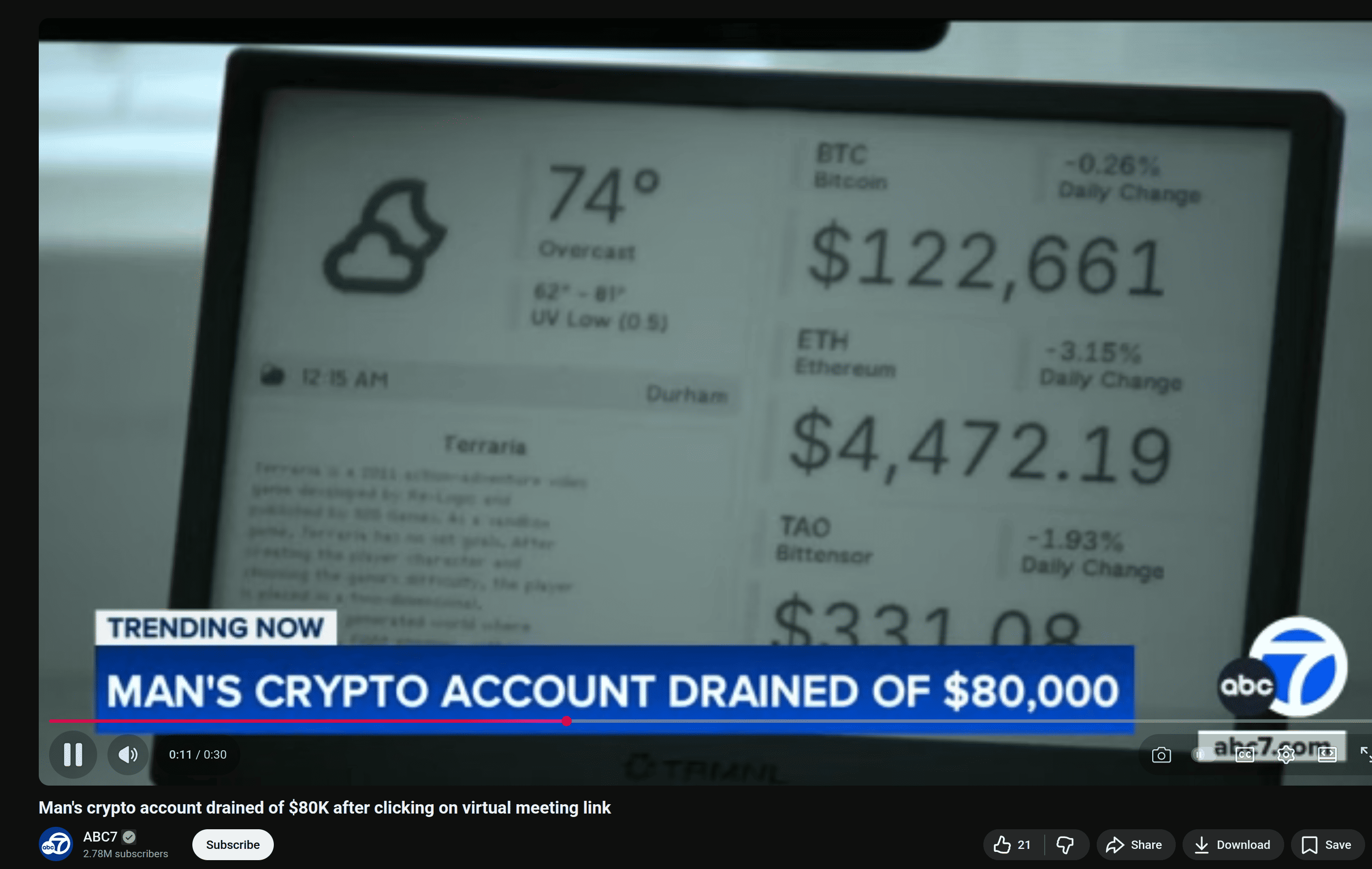
There have been many cases where attackers exploited victims through video meetings, especially when using outdated or vulnerable conferencing tools like Zoom with known RCE (Remote Code Execution) CVEs. In several incidents, hackers also convinced targets to install fake “meeting enhancements” or Zoom extensions that were actually malware, giving them full access to the victim’s device.
| # | Hack Name / Incident | Amount Stolen | Source / Verification |
|---|---|---|---|
| 1 | $6.09M GIGA Memecoin Whale Drain Fake Zoom invite → phishing site → private keys stolen |
$6.09 million | CryptoNews | CoinTelegraph |
| 2 | $1.35M THORChain Co-Founder Deepfake Zoom North Korean Lazarus group — deepfake video call + iCloud Keychain hack |
$1.35 million | Crypto.news | Yahoo Finance |
| 3 | $1M+ SlowMist Fake Zoom Malware Campaign app.us4zoom.us → malicious ZoomApp.dmg for macOS |
~ $1 million | SlowMist Report | DeFi Planet |
| 4 | Hypersphere VC Partner Life-Savings Drain Mehdi Farooq — hijacked Telegram → fake Calendly → Zoom malware |
$1M+ (seven figures) | CoinTelegraph | AInvest |
| 5 | Fake Zoom “Endless Loading Screen” Malware Tricks users into downloading malware while “waiting for host” |
$300K+ across victims | CoinTelegraph | Decrypt |
One of a notable hack is Thorchain co-founder losts $1.35M due to a deep fake + Zoom link scam

https://www.coinspeaker.com/thorchain-cofounder-loses-1-3m-deepfake-scam/
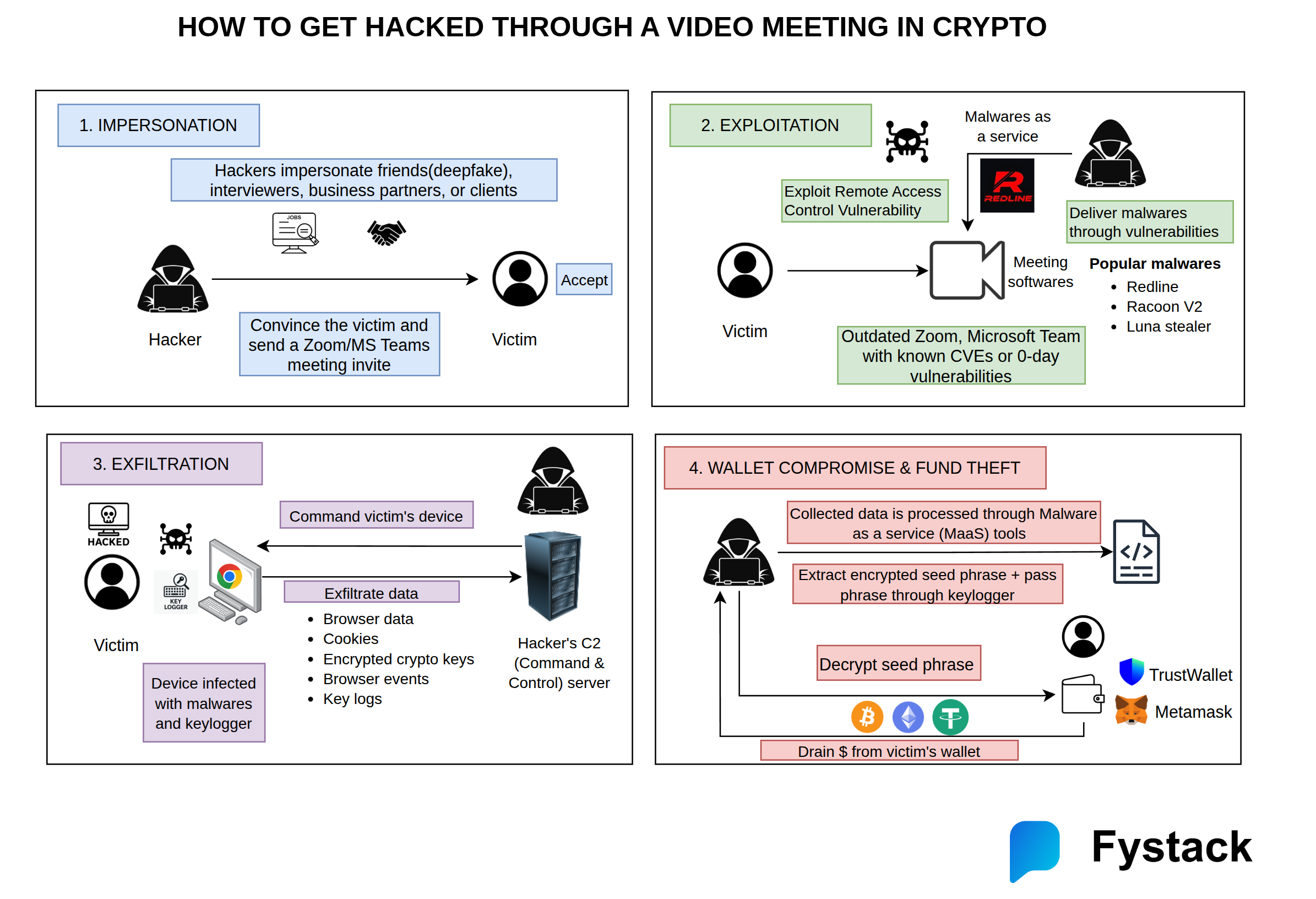
Multi-step process to hack someone through a video meeting in crypto
Attackers don’t just rely on one trick — they combine social engineering, software exploits, and malware toolkits to compromise wallets and drain funds. Below is a clear breakdown of the multi-step process used in real-world crypto-targeted video-meeting attacks.
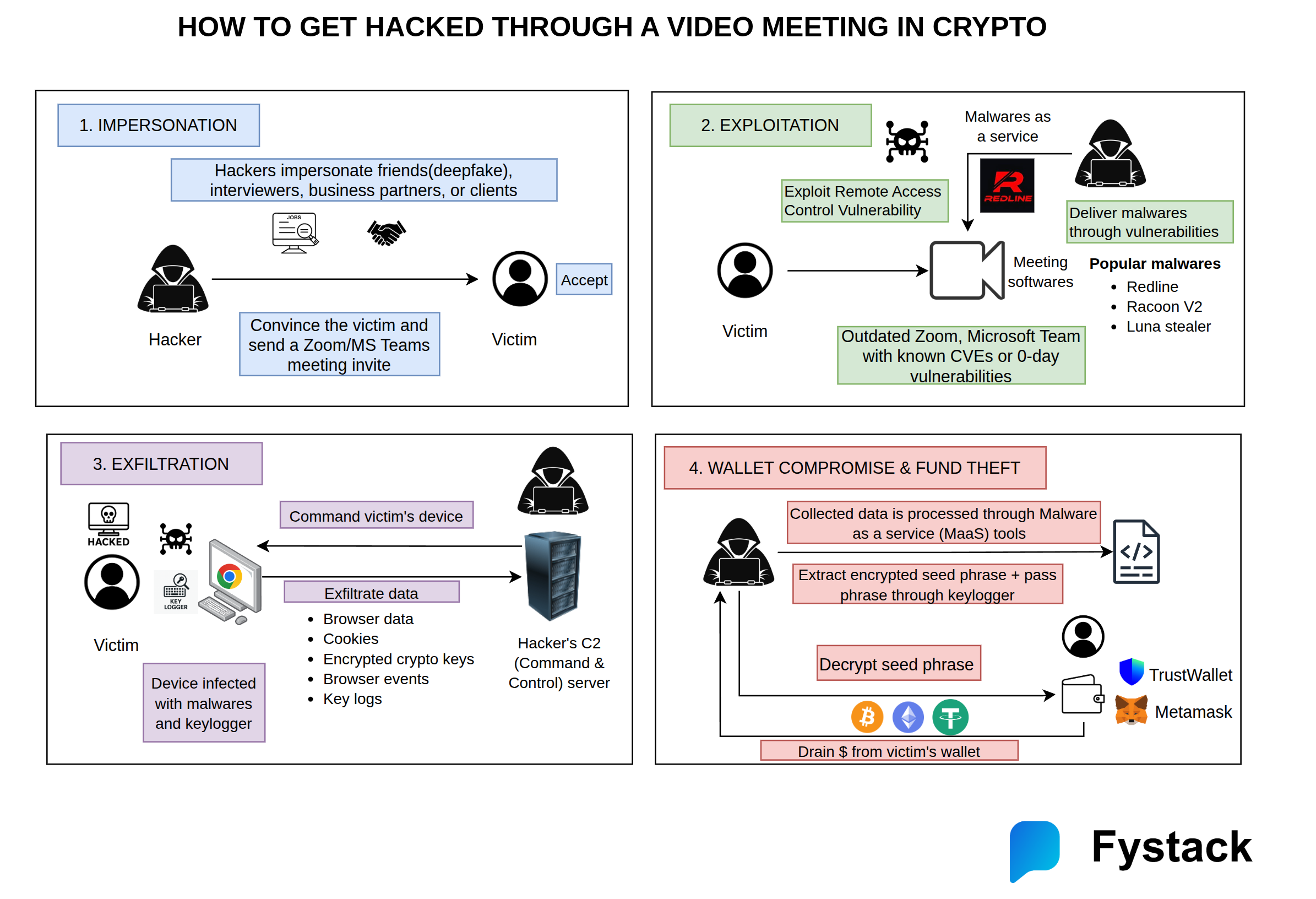
1. Impersonation
Hackers begin by pretending to be trusted individuals: interviewers, investors, business partners, clients, or friends.
They use convincing pretexts and may even leverage deepfake video or voice to build trust.
Once rapport is established, they send a Zoom or Microsoft Teams meeting invite, framing it as a professional discussion (e.g., job interview, partnership call, demo).
Goal: Get the victim into a controlled environment where exploitation becomes possible.
2. Exploitation
During the meeting, attackers attempt to compromise the victim’s device using:
- Outdated Zoom/Teams clients with known CVEs
- Privately sold 0-day vulnerabilities
- Remote Access Control weaknesses in meeting software
They deliver malware using Malware-as-a-Service (MaaS), often through hidden payloads embedded in shared files, screen-share exploits, or simply by triggering a vulnerability in the outdated video client.
Common malware used:
- Redline
- Racoon V2
- Luna Stealer
Goal: Achieve initial infection with infostealers and keyloggers.
3. Exfiltration
Once malware is active, the attacker’s Command-and-Control (C2) server silently takes over.
Stolen data includes:
- Browser cookies
- Sessions and login tokens
- Saved passwords
- Encrypted crypto wallet files
- Key logs (typed seed phrases, passwords)
- Browser events and autofill data
The malware constantly exfiltrates data in the background, giving attackers everything they need to decrypt wallet secrets.
Goal: Collect sensitive data that leads to full wallet compromise.
4. Wallet Compromise & Fund Theft
With enough exfiltrated data, attackers process the stolen information using MaaS dashboards that automatically:
- Identify crypto-related credentials
- Extract encrypted seed phrases
- Match them with keylogger-captured passphrases
- Reconstruct private keys
Once they decrypt the seed phrase, they import the victim’s wallet (MetaMask, Trust Wallet, etc.) and transfer assets out.
Funds are usually laundered immediately through mixers, CEX accounts, cross-chain swaps, or private OTC channels.
Goal: Drain the victim’s assets as quickly as possible.
Hack scenarios
Scenario 1: Hacked Telegram Account + Deepfake Friend (similar to the Thorchain-style attack)
A victim’s close friend has their Telegram account compromised. The attacker uses the hijacked account to message the victim, claiming there’s an urgent call about a new partnership or deal. Because the message comes from a trusted friend, the victim joins the meeting link without suspicion.
Inside the video call, the hacker appears as a deepfaked version of the friend, using AI-generated video and voice cloning to perfectly mimic their appearance and tone. Once the victim is on the call, the attacker silently exploits a 0-day vulnerability or a known RCE CVE in Zoom.
This allows the attacker to execute malicious code directly on the victim’s machine without requiring any downloads or extensions. Through the exploit, the attacker installs malware that harvests private keys, clipboard data, password autofill sessions, and authentication tokens, giving them everything needed to drain wallets and breach other accounts.
Scenario 2: Executive Impersonation to Trick Employees (deepfake voice + fake Zoom extension)
Attackers impersonate a C-level executive from the victim’s company. Using publicly available videos and interviews, they generate a deepfake voice and a prerecorded facial animation.
They message an employee about a high-priority meeting. During the call, the “executive” urgently asks them to install a Zoom extension to “access the shared dashboard.”
The extension is a credential-stealing payload that compromises internal systems and wallet infrastructure.
Scenario 3: Fake Investor Pitch With Deepfake VC Partner
Scammers pose as a well-known VC fund and send a meeting request to a crypto founder. They use convincing email domains, LinkedIn profiles, and Calendly invites.
During the call, a deepfake video of a “partner” explains they can’t turn on audio properly due to travel, asking the founder to install a meeting plugin to “enable real-time pitch deck rendering.”
The plugin infects the founder’s device and exfiltrates API keys, Relay nodes tokens, and wallet credentials used in product demos.
How to Protect Yourself
- Use browser-based meetings (Zoom Web, Google Meet, Teams Web). Browsers run in a sandbox, giving attackers far less access than desktop apps.
- Don’t install anything during or before calls: no plugins, no “interview tests,” no shared executables.
- Keep meeting apps updated if you must use the desktop version.
- Never allow screen control or remote access from strangers.
- Use a separate device or browser profile with no wallets installed when joining calls.
- Store funds in hardware or MPC wallets so malware can’t access private keys.
Stay Safe. Build Securely
Fystack is building enterprise-grade wallet infrastructure for teams, powered by MPC technology to eliminate single points of failure, prevent key theft, and protect organizations from modern attack vectors like video-meeting exploits and infostealers.
If you care about security, compliance, and reliability in Web3 operations:
👉 Try Fystack today: https://app.fystack.io
👉 Join our Telegram community for web3 security updates, engineering insights & product updates: https://t.me/+9AtC0z8sS79iZjFl