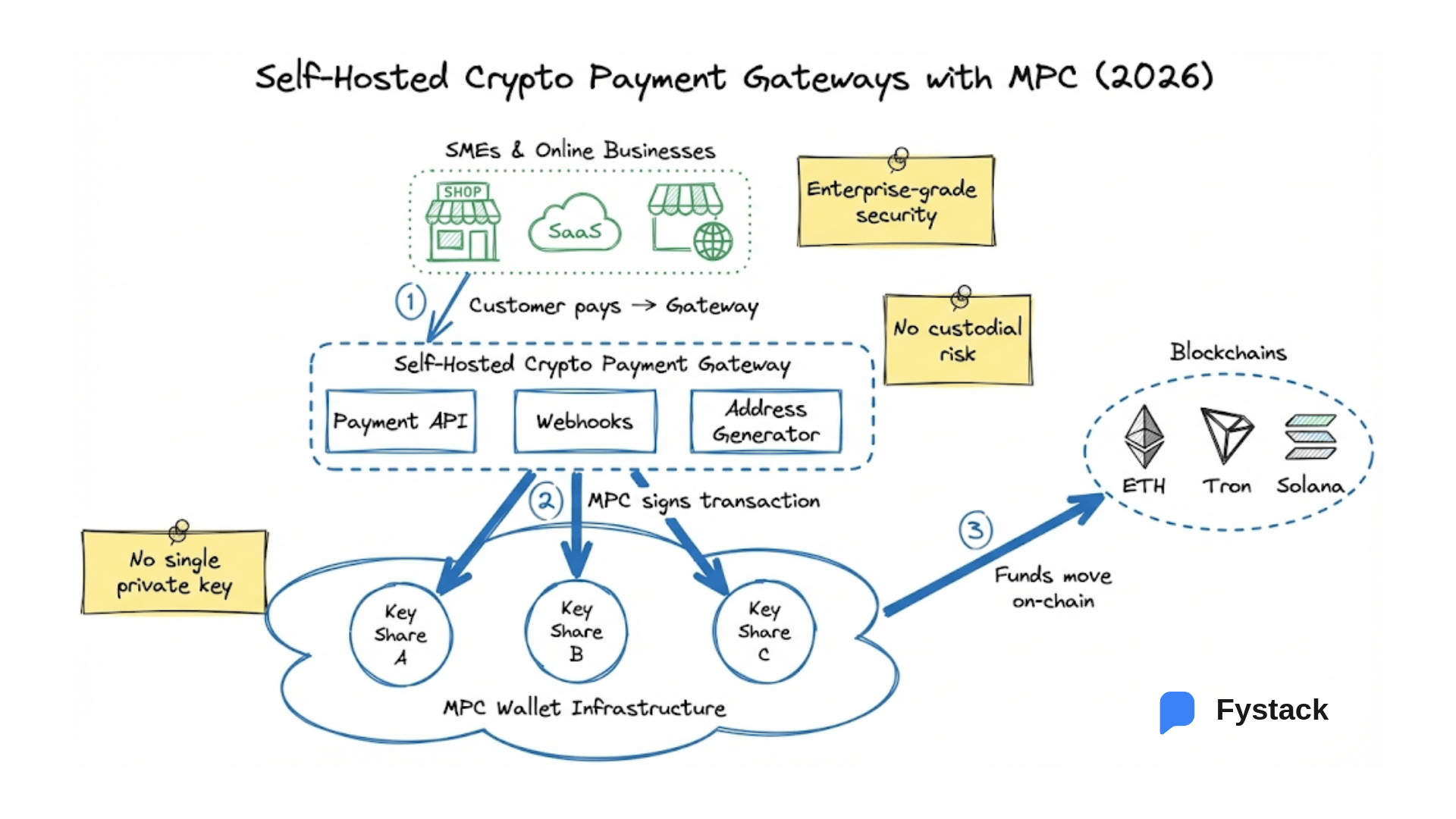
The New Standard in 2026: Self-Hosted MPC Wallet Infrastructure
Ted Nguyen
Author
BD & Growth @Fystack

The $600+ Billion Question: Who Do You Trust With Your Digital Assets in 2026?
Think securing digital assets is just a small corner of the crypto world? Let's check the numbers, because they might just blow your mind.
The overall Digital Asset Custody market – everything involved in keeping digital money safe, from cold storage to advanced wallet infrastructure – is massive. We're talking about $684B in 2024, according to GrandView Research .
So, if you’re asked what is the market size of Digital Asset Custody? The answer is $684B.
Another question could arise is, how big is the Digital Asset Custody market? It's 14 times bigger than the RWA tokenization market and twice the size of the entire stablecoin market combined.
Within that vast custody landscape, the global MPC (Multi-Party Computation) market stood near $888M in 2024, according to Scalable Solutions.
Finally, a subset of it: the MPC Wallet Development market was valued at USD $61.4M in 2024, according to Intel Market Research. This is the critical layer providing the open-source toolkits and infrastructure.
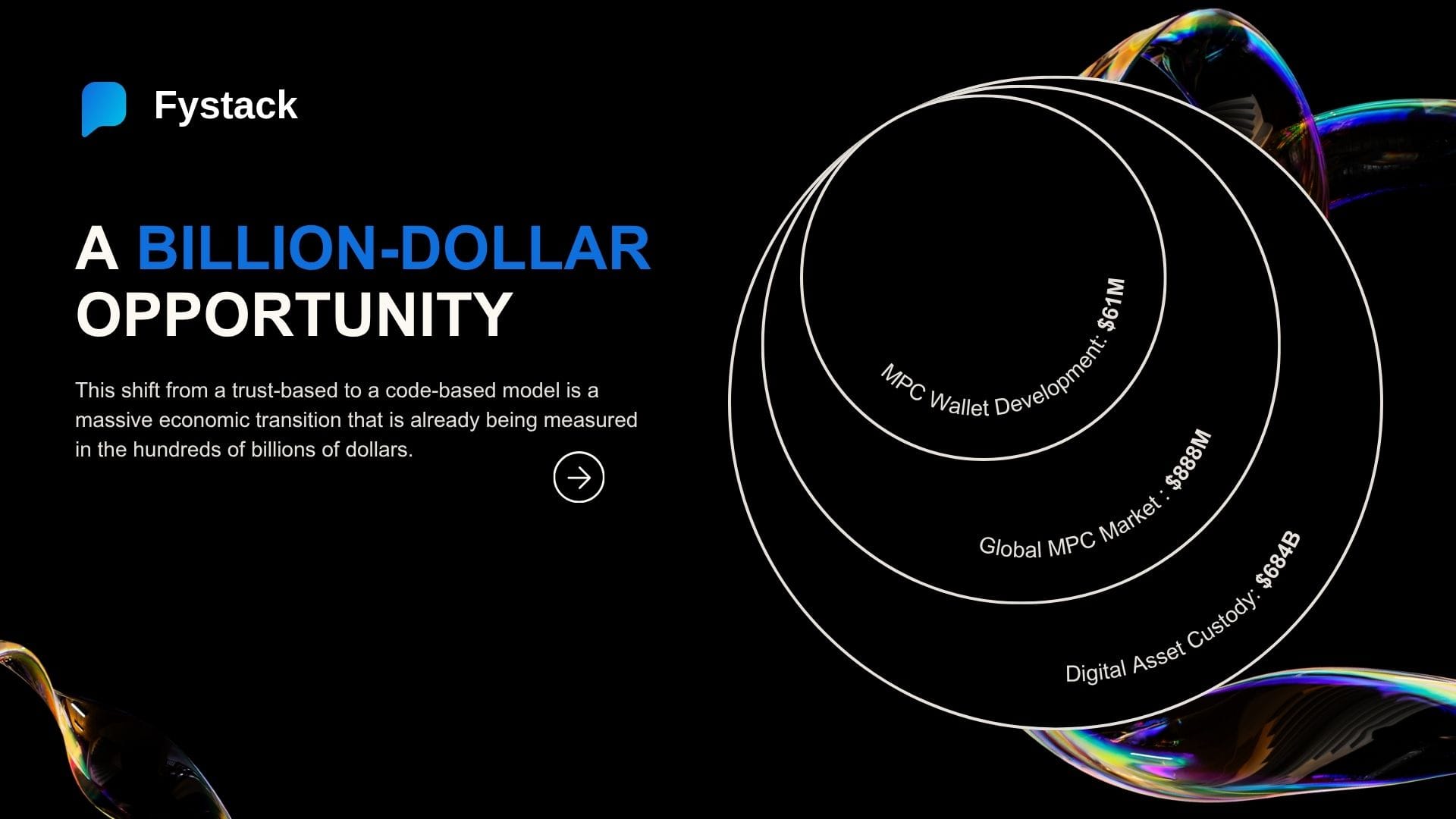
Clearly, the demand for secure, scalable, and controllable infrastructure is standard.
Perhaps you're exploring this critical infrastructure layer yourself, asking questions like:
- What is a self-hosted MPC wallet infrastructure?
- Which security risks are addressed by using MPC wallets?
- Why should I choose a self-hosted MPC wallet infrastructure over traditional wallet solutions?
Understanding the answers is key, because they point towards a fundamental change happening as we move deeper into 2026...
The Shift From Trust-Based to Verify-Based Control
For centuries, the world we live in has run on a single, unspoken principle: trust.
It’s so obvious that we rarely pause to question it. In fact, it’s with us from the day we’re born.
As a child, you have no choice but to trust the vaccines provided by health authorities. As you grow, you trust the food you buy at the supermarket, you trust the banking system will protect your savings, and you trust that the education system is teaching you something valuable.
This trust is built on reputation, complex legal agreements, and manual, human-driven processes. The entire system works because we agree to place our faith in these established institutions.
But here’s the problem: trust is often not a two-way street.
You trust them, but do they always have your best interests at heart?
They say they keep your money safe, but banks use your deposits for fractional reserve lending to earn massive profits for themselves. We saw this break down spectacularly with the collapse of FTX, where billions in customer funds were secretly gambled away, highlighting the risks in traditional digital asset security models.
Indeed, the scale of recent security breaches underscores this vulnerability. Just last year, we witnessed how exchange security operations failed us, sending a stark warning to the industry.
(Read more: 2025: The Year Crypto Exchanges Got Hacked — And Why Exchange SecOps Is Failing Us)
You’ve also seen how SaaS-based wallet infrastructure providers promise convenience and efficiency for a "small" fee. But as your business grows and becomes more dependent on them, you realize you're trapped in their ecosystem. Suddenly, you're not a customer anymore. You're a captive, feeding their recurring revenue model with no easy way out.
But what if there was another way? A decade ago, a new philosophy emerged from the world of blockchain and Distributed Ledger Technology (DLT). It's a simple, yet radical idea:
"Don't trust, verify."
In this world, "code is law," and transparency is the fundamental characteristic. Wallet security comes from the ability of anyone to audit the logic and verify that it functions exactly as promised.
In 2026, the digital asset market is at a critical point where institutional customers are actively seeking ways to operate on-chain. But they cannot simply abandon their rigorous security standards.
In other words, this market [digital asset custody] needs a solution that is both secure, but also transparent and auditable, enabling true Self-custodial Wallet models.
This is the inevitable shift we're witnessing: the transition from trust-based to verify-based control. And in this transformation lies a massive opportunity. The key to unlocking it isn't another trusted institution, but a new kind of verifiable technology: self-hosted, open-source MPC infrastructure.
This article will break down why this shift is happening now and make the case that this critical technology is the bridge for serious businesses to confidently enter the on-chain world.
Why Verify-Based Models Matter for On-Chain Business in 2026
I declare that: for any serious business looking to operate on-chain, the "verify-based" model solves three fundamental challenges that the old "trust-based" system simply can't.

Transparency Challenges in SaaS Wallet Trust Models
Normally, when a business uses a SaaS wallet provider, they trust. They trust the brand reputation, testimonials, and importantly trust other institutions that issue their security certifications (SOC 2, ISO,...).
You trust that their internal security is sound, but you can never truly verify it yourself.
That’s the old way. With verify-based, it turns to the opposite story.
With a self-hosted, open-source infrastructure, you do not need to force yourself to believe in a thing. Right now, it is verifiable.
Your own engineering teams can audit every line of code. They can see for themselves the exact cryptographic protocols being used and how security policies (policy enforcement) are implemented.
This is the difference between simply having to trust that a vault is secure, versus being able to verify it yourself with the actual plans, moving towards a zero-trust architecture.
For a deeper dive into this comparison, check out our analysis on Fystack vs Fireblocks – Self-Hosted vs SaaS.
Regulation & Compliance
The arrival of comprehensive regulations like the EU's MiCA is a sign of a maturing industry. But it also creates a massive challenge for businesses built on a trust-based model.
How do you prove compliance to a regulator when your entire security stack is controlled by a third-party SaaS provider?
When you run your own infrastructure, you achieve auditability without sacrificing control.
For example, in the case of data sovereignty when you need to comply with data residency laws? You can choose to run your servers in a specific location to meet the requirements.
Is it possible for most SaaS providers? You could answer that by yourself.
This capability is becoming crucial as banks and fintechs build new settlement rails.
See: What Are Tokenized Deposits? Why Banks Are Building New Settlement Rails
Scalability & Automation
Trust-based systems are limited by human scale. It requires multiple emails, phone calls, and manual checks to approve a large corporate payment or manage digital asset transactions.
The process is slow, expensive, and prone to error.
With verify-based control, you could define your business logic as code within your own MPC infrastructure, leveraging Policy Engine workflows. This allows for "Just-in-Time" liquidity and automated reconciliation across global operations.
You can automate complex processes with perfect precision, implementing features like role-based permissions seamlessly.
We already helped businesses from being desperate by the process to successfully take advantage of this Secure Asset Management approach.
You can check our case study in which Fystack helps Gaian to grow with 60% in time savings, and zero manual errors with MPC digital wallet infra.
Overall, these are automated, policy-based workflows that execute instantly and flawlessly, 24/7.
The MPC Wallet Infrastructure is Ready
One more important factor that drives this transformation is the maturity of Secure Multi-party Computation (MPC) Technology.

If you looked into Multi-Party Computation (MPC) a few years ago, you might have walked away thinking it was a fascinating cryptographic concept, but too slow and complex for the real world.
And back then, you would have been right. But the game has completely changed. Multi-Party Computation (MPC) in its prime time right now.
First, recent protocol improvements have greatly increased transaction signing speeds. This means Multi-Party Computation (MPC) can now easily handle high-volume uses in gaming, fintech, and cross-border stablecoin payments.
Second, implementing MPC right now doesn’t require a PhD level cryptographers anymore. The technology today has matured into accessible, battle-tested libraries and platforms.
It relies on proven concepts like threshold cryptography and specific threshold signature schemes.
Major companies like Binance show the field's maturity by open-sourcing their core tss-lib, a ready-to-use library for distributed key generation (DKG protocols) and signing using ECDSA protocols.
“When industry giants start sharing their foundational code, you know the technology is stable.”
This accessibility has reached a new level. For example, Fystack's own MPC engine, Mpcium, offers production-ready MPC nodes that simplify key management and can be deployed within days, not months.
Read the founder's story: Why We Built Mpcium
Lastly, regulations like the EU's Markets in Crypto-Assets (MiCA) and updated U.S. SEC custody rules require strong, secure wallet infrastructure for institutions.
MPC technology is a natural solution. It's designed to create powerful, code-enforced security rules essential for managing corporate governance and achieving high fault tolerance and effective disaster recovery models (Unlike relying solely on hardware wallets or basic hot wallets which have their own limitations.).
For instance, MiCA requires crypto-asset custodians to implement appropriate technical and organisational measures to securely manage private keys with transparency and auditability.
If you're still unsure about MPC Technology, read our blog on why your company should choose MPC Wallets to go on-chain.
The Fall of SaaS: Self-hosted Solution is Growing
So, by now, you probably understand the core differences between a SaaS wallet and a self-hosted one.
But just in case you still don't trust me... well, that's okay. In fact, you're doing exactly the right thing.
But let me ask you this: You don't trust me, so why do you still trust a SaaS provider?
At its core, a SaaS-based wallet infrastructure platform is still a trust-based model (think of platforms like Fireblocks Wallet-as-a-Service). You are trusting their code, their servers, their security team, and their business integrity.
If you're serious about building on-chain, it's time to shift your mindset to a verify-based one. And the only way to achieve true, verifiable, verify-based control is to self-host your MPC wallet infrastructure.
Read our documentation on how you can self-host with Fystack.
Understanding the different approaches available, especially non-custodial solutions for key assets like stablecoins, can help clarify this decision. Check out our latest article on Top5 Non-Custodial Solutions for Stablecoin Businesses
Own Your Security Foundation in the Verify-Based Era
The shift from trusting intermediaries to verifying code is the most critical strategic transition for businesses building in Web3. It impacts your security, your ability to comply with regulations, your operational scalability, and ultimately, your competitive advantage.
Relying on trust-based SaaS wallets leaves you vulnerable and dependent.
It’s now the most suitable time for your business to embrace verify-based control through self-hosted, open-source MPC infrastructure. You’re about to build a future where your digital asset operations are secure, transparent, scalable, and fully under your cryptographic control.
Ready to take control? Make your decision now!
First, sign up for Fystack now for exclusive access
Then, join our Telegram Community (300+ members) to connect with our team and other builders exploring the future of self-hosted MPC.
Frequently Asked Questions (FAQs)
Why should I choose MPC over Multi-sig?
Unlike Multi-sig, which requires specific smart contracts for each blockchain, MPC is chain-agnostic, working seamlessly across Solana, EVM, and non-EVM chains without extra integration. Additionally, MPC operates off-chain, significantly reducing gas fees and ensuring operational privacy, as your internal approval structure remains hidden from the blockchain.
How does Fystack support on-premise deployment?
We provide end-to-end implementation. The Fystack team assists with full deployment to ensure your infrastructure is secure from day one. We also commit to high reliability through clear SLAs and offer dedicated technical support to handle upgrades, troubleshooting, and maintenance, ensuring your operations never miss a beat.
What is the core difference between SaaS and Self-hosted MPC wallets?
The difference lies in control. SaaS is a "Trust-based" model, where you must rely on the vendor's security. Self-hosted is "Verify-based," giving you absolute ownership of the source code. This ensures you have total control and eliminates the risk of vendor lock-in.
How does Self-hosted MPC help with regulatory compliance (e.g., MiCA)?
It directly addresses Data Sovereignty. Self-hosting allows you to physically locate servers in jurisdictions required by law and enables you to audit your entire security process at any time which SaaS solutions cannot provide.
How large is the Digital Asset Custody market currently?
The market represents a massive opportunity, valued at approximately $684 billion in 2024. To put that in perspective, this is 14x larger than the Real World Asset (RWA) market and double the total market capitalization of all stablecoins combined, as of January, 1, 2026.