Open Source MPC Wallet Infrastructure: MPCium v0.3.3 – Enhanced Decentralization with Multi-Authorizer Support
Thi Nguyen
Author
Founder
The security of digital assets is the cornerstone of the Web3 ecosystem, yet traditional methods of key management remain a significant challenge. Single points of failure, such as a compromised private key or a lost seed phrase, can lead to irreversible losses. While solutions like multisig and hardware wallets have offered improvements, they introduce their own complexities and limitations. The industry is rapidly converging on a more robust and flexible cryptographic paradigm: Multi-Party Computation (MPC).
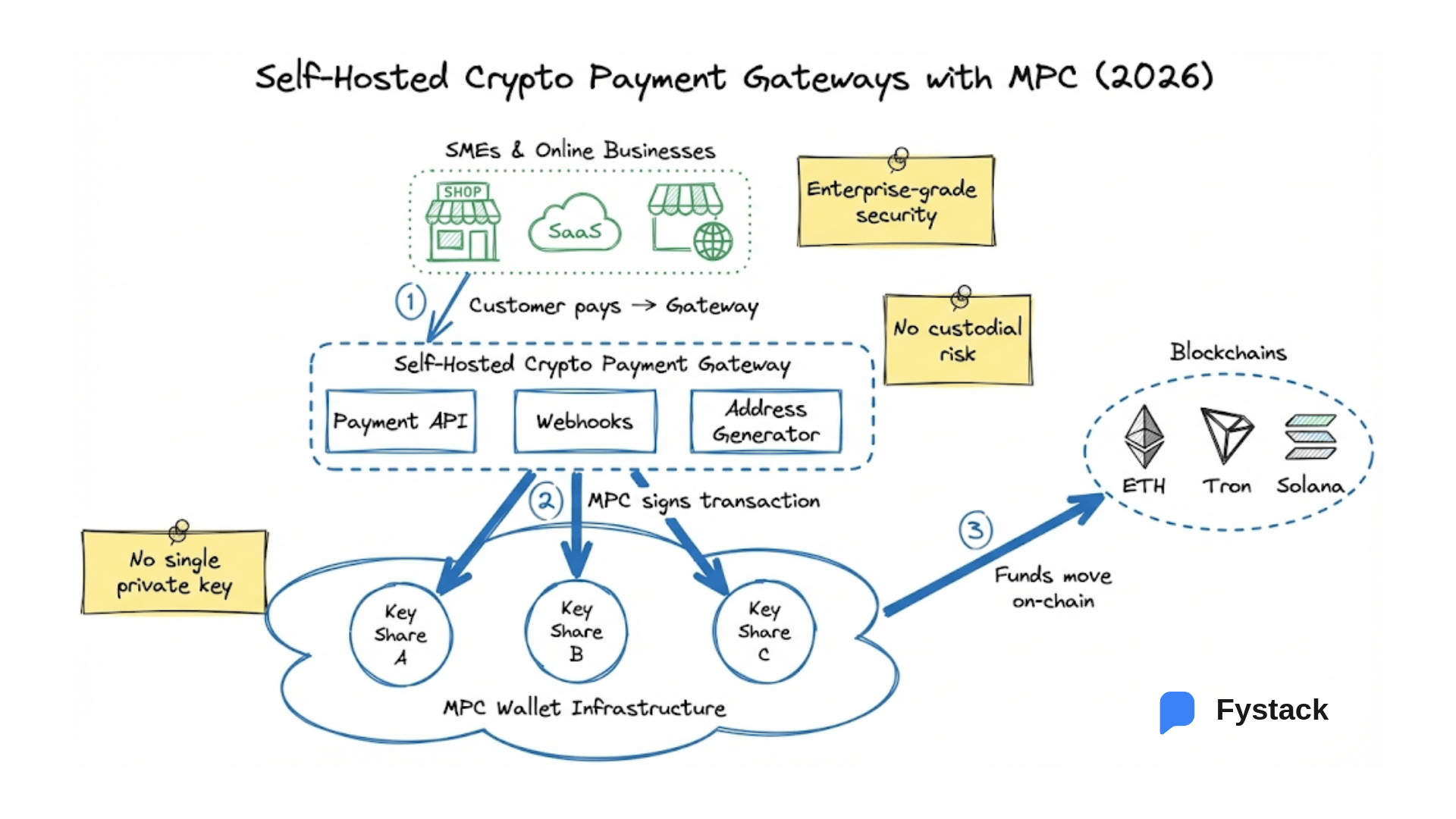
What is MPC? MPC (Multi-Party Computation) is a cryptographic technology that splits a private key into multiple independent shares stored across different devices or locations.
At no point is the private key ever fully reconstructed, eliminating single points of failure and greatly improving security. This makes MPC wallets ideal for business use cases and institutional crypto custody, where reliability, decentralization, and compliance are top priorities.
Fystack has been developing an open source MPC wallet infrastructure called Mpcium that allows developers to effortlessly spin up MPC nodes and generate MPC wallets without complex setup.
The goal is to make secure, self-hosted MPC technology accessible for developers and enterprises, enabling them to build compliant custody systems or integrate MPC signing directly into their applications.
Over the past few weeks, we’ve received amazing feedback from the community to improve decentralization, reliability, and compliance in our open source MPC node, MPCium on GitHub.
This release builds on that foundation with new features and performance improvements designed for scalable, production-grade deployment.
👉 Check out the previous release:
Fystack Release: MPCium v0.3.2 – DH Key Exchange & AWS KMS Support
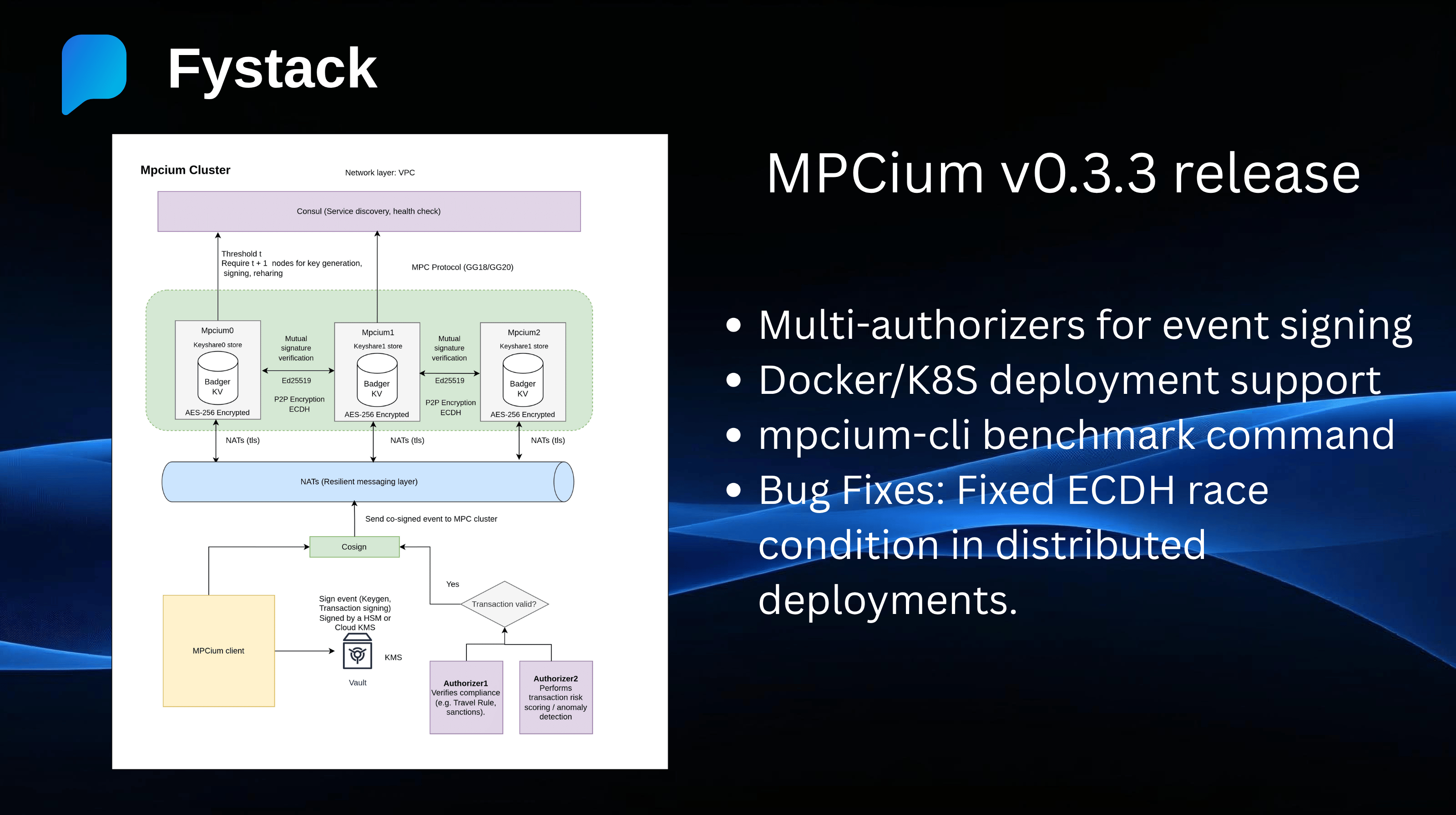
Docker & Kubernetes Deployment Support
MPCium nodes are now fully containerized!
You can deploy your MPC wallet infrastructure seamlessly on Docker Compose or Kubernetes.
Follow the full deployment guide:
https://github.com/fystack/mpcium/blob/master/deployments/kubernetes/k8s-instruction.md
This enhancement makes it easier for developers to spin up multi-node MPC clusters with proper health checks, restart policies, and cloud-native observability.
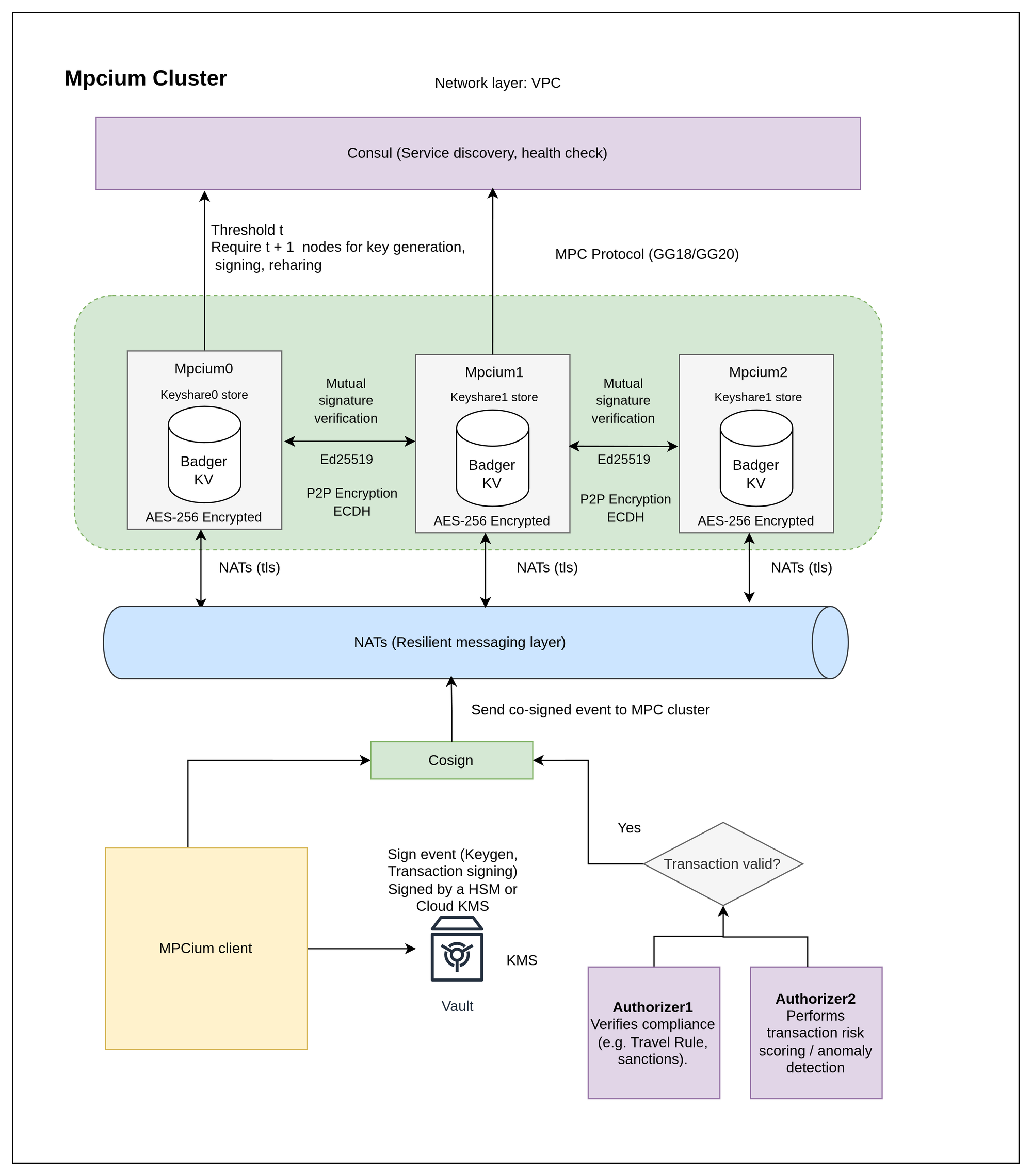
Multi-Authorizer Configuration for Keygen, Signing, and Resharing
To improve decentralization, compliance, and travel rule compatibility, MPCium v0.3.3 introduces multi-authorizer co-signing.
You can now configure authorizers that must approve key generation, signing, or resharing operations.
Example configuration
authorization:
enabled: true
required_authorizers:
- authorizer1
- authorizer2
# Authorizer public keys configuration (applies to all operations: keygen, signing, reshare)
authorizer_public_keys:
# Example:
authorizer1:
public_key: "4711ec2728feb66f223078140323e0947a70a5fa36615c21382c2a9bc9241524"
algorithm: "ed25519"
authorizer2:
public_key: "33d5b5b3973c9bd46d782bc5488ea1840188234b0cbed66153b691caafe85385"
algorithm: "ed25519"This feature gives enterprises and custodians more flexibility to enforce internal approval policies and integrate KYT (Know-Your-Transaction) and compliance checks directly into MPC workflows.
Performance & Benchmarking
We’ve added a new mpcium-cli benchmark tool that allows developers to test the performance of MPCium clusters easily.
# Test wallet creation
mpcium-cli benchmark keygen 10
# With config and output file
mpcium-cli benchmark --config config.yaml --output results.txt keygen 50⚡MPC at scale
— Fystack (@fystack) September 20, 2025
Our team is cooking mpcium-benchmark cli tool to let you stress-test your local or cloud #MPC cluster.
Traditional MPC engines are slow, with high latency and node-synchronization issues.
Our MPC engine can sign thousands of transactions simultaneously.
Sign your… pic.twitter.com/kSvTWcER5y
Demo of MPCium benchmark-cli
This lets teams measure throughput and latency for keygen, signing, and resharing operations under various network setups.
Bug Fix: ECDH Race Condition in Distributed Deployments
We fixed an issue where nodes could get stuck during bootstrapping in distributed environments.
In earlier versions, the ECDH key exchange occasionally retriggered indefinitely, preventing the MPC cluster from becoming ready.
Observed Symptoms
Node0 (successful):
23:12:41 - Register peerID=a8d392dd-9913-4ebe-8c52-4848cc84b962
23:12:41 - All peers are ready including ECDH exchange completion
23:12:42 - SigningConsumer: Sufficient peers ready, starting message consumption
23:12:44 - KeygenConsumer: All peers are ready, proceeding to consume messages
Node1 & Node2 (stuck):
23:13:38 - Starting to broadcast DH key nodeID=c4ee7396-9a72-4735-ab2e-a785b68d2bc0
23:13:43 - [ECDH exchange retriggerd] not all peers are ready
23:13:48 - [ECDH exchange retriggerd] not all peers are ready
23:13:53 - [ECDH exchange retriggerd] not all peers are ready
(repeats indefinitely...)The issue is fixed in the PR https://github.com/fystack/mpcium/pull/111
Acknowledgements
Building distributed systems like MPC nodes is both time-consuming and resource-intensive.
We’re deeply grateful for the community’s continued contributions and testing efforts.
Special thanks to new contributors: sivo4kin johnnynanjiang
If you want to stay updated on future MPC wallet infrastructure releases or join engineering discussions: https://t.me/+IsRhPyWuOFxmNmM9
Learn More
- Read more about why MPC is essential for business wallets
- Explore open source MPC wallet infrastructure for enterprise custody
- Visit fystack.io/blog for more engineering deep dives
 FystackFystack
FystackFystack
 FystackFystack
FystackFystack
 FystackFystack
FystackFystack